Securing 3rd party API Integrations
Prophaze offers a wide range of cybersecurity solutions, including securing third-party API integrations. Helps to identify and mitigate potential security
Prophaze offers a wide range of cybersecurity solutions, including securing third-party API integrations. Helps to identify and mitigate potential security

The conventional Model is WAF 1.0 Hardware-driven, not scalable, typically rule-based architecture which came into existence in the early 2000s.
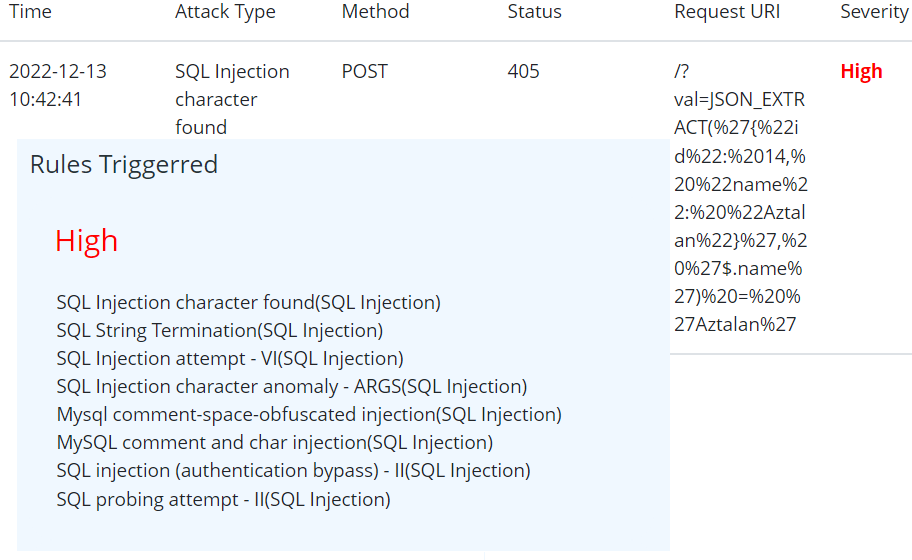
A New WAF Bypass hack has been identified by claroty team. This uses json based sql strings which is not conventionally been
Features Prophaze Array Networks Architecture Purely Software-Defined WAF (SDWAF) Hardware defined Solution Microservices Support Kubernetes and Microservices Support Legacy Deployment
Features Prophaze F5 OWASP top 10 Yes Yes SANS top 25 Yes Yes IP reputations and blacklist and whitelist Yes
Features Prophaze WAF (Explorer) Imperva Cloud WAF (Pro Version) Architecture ML/AI-Based WAF Custom rule based WAF Microservices Support Kubernetes and
Cloudflare Enterprise Prophaze Enterprise All Prophaze Business Features Web application firewall (WAF) with unlimited custom rulesets Unlimited Rule Sets +
Cloudflare Business Prophaze Business All Prophaze Pro Features Web application firewall (WAF) with 25 custom rulesets ML Based WAF with
Cloudflare Pro Prophaze Explorer Fast, easy-to-use DNS DNS is changed at Existing DNS Manager (Fast Propagation) Free automated SSL certificates
These are the Best API security Practices to secure exposed APIs from getting hacked Only expose that which is required
The Prophaze Cloud WAF is built natively on the Kubernetes Platform and protects clients’ Kubernetes clusters and cloud infrastructure from

Prophaze WAF can protect Java-based Applications that are prone to recent log4j vulnerability. Prophaze is pre-equipped with live signatures of

There are many products out there that work as a WAF. WAF is not really aware of the application it

Overview : Remote Code Execution vuln in Zend Framework 3.0.0 Affected Product(s) : Zend Framework 3.0.0 Vulnerability Details : CVE

Overview : Tenda N300 allows Authentication Bypass vuln through Malformed HTTP Request Affected Product(s) : N300/N301 Router Vulnerability Details :

Overview : Multiple vulnerabilities like Unprotected AJAX Action & Cross-Site Request Forgery reported in XCloner Affected Product(s) : versions before

Overview : Pure-FTPd 1.0.48 allows remote attackers to prevent legitimate server use by making enough connections to exceed the connection

Overview : DoS vulnerability in the file upload request feature of Atlassian Crucible Affected Product(s) : version < 4.7.4 4.8.0

Overview : HCL BigFix Inventory does not enforce “secure” attribute for SSO related cookies when SSO is enabled. Web browsers

Overview : Online Bus Ticket Reservation 1.0 – SQL Injection Affected Product(s) : Version: 1.0 Vulnerability Details : CVE ID

Overview : Multiple vulnerabilities reported in BIG-IP Traffic Management User Interface Affected Product(s) : BIG-IP versions 16.0.0 – 16.0.0.1 BIG-IP

Overview : XSS issue in Gitlab CE/EE Affected Product(s) : from 12.4 before 13.4.7, 13.5 before 13.5.5, and 13.6 before

Overview : Multiple vulnerabilities reported in AEM’s Cloud Service offering Affected Product(s) : AEM Forms SP6 add-on for AEM 6.5.6.0

Overview : XSS issue in WebUI Translation in Systran Pure Neural Server Affected Product(s) : Systran Pure Neural Server before