AI Firewall Defends From AI Attacks
Most Effective Way to Defend from AI attacks
Prophaze’s AI Firewall is designed to be easy to deploy and manage, with features such as auto-scaling and auto-tuning to optimize performance and minimize false positives. In order to provide a more thorough security posture, AI firewalls can also connect with other security technologies, including as intrusion detection systems (IDS) and security information and event management (SIEM) solutions.


Advanced Security Solution for Businesses
Prophaze AI Firewall is important for businesses to have because cyber threats are becoming more sophisticated and traditional security solutions are no longer adequate to protect against them. Prophaze AI Firewall provides businesses with an advanced security solution that can detect and block cyber threats in real time, helping to prevent data breaches, financial losses, and damage to reputation. Prophaze AI Firewall is an essential tool for businesses looking to protect against cyber threats and improve their security posture in an increasingly digital and interconnected world.
Detection and Blocking Real-time Cyber Threat
Easy Deployment Process
Organizations are migrating to Kubernetes but also exposing containerized applications to new security blind spots and attack surfaces that may compromise their entire IT systems. It blocks cyberattacks, mitigates vulnerabilities, and shares threat intelligence to close gaps in your enterprise-wide security coverage with existing security products such as endpoint protection, SIEM, and SOAR.
In order to effectively protect against cyber threats, the deployment procedure for Prophaze AI Firewall entails assessing the network environment, selecting a deployment option, installing and configuring the instance, testing the deployment, and monitoring and maintaining the instance.
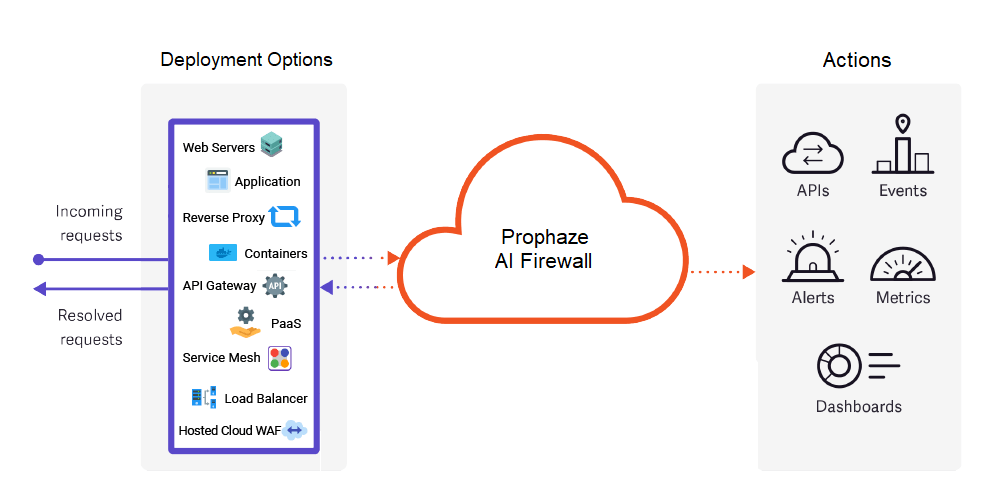
Prophaze levels the playing field for security teams with an AI-powered autonomous firewall.
Prophaze AI Firewall's Use of AI and Machine Learning Algorithms
Prophaze AI Firewall integrates machine learning and AI algorithms to quickly detect and prevent threats on the internet. Security solutions include behavioral analysis, deep packet inspection, threat intelligence, adaptive learning, and automated response. By utilizing AI and machine learning techniques, the Prophaze AI Firewall can identify threats more quickly and precisely than traditional rule-based methods..
