What is meant by Broken Access Control?
Broken access control is the first category in OWASP Top 10 web application security threats and hence a critical issue that can impact the security of web applications. Access control refers to the process of granting or denying user access to resources based on their identity and privileges. Broken access control occurs when web applications do not properly implement access control mechanisms, allowing users to access resources they should not have access to.
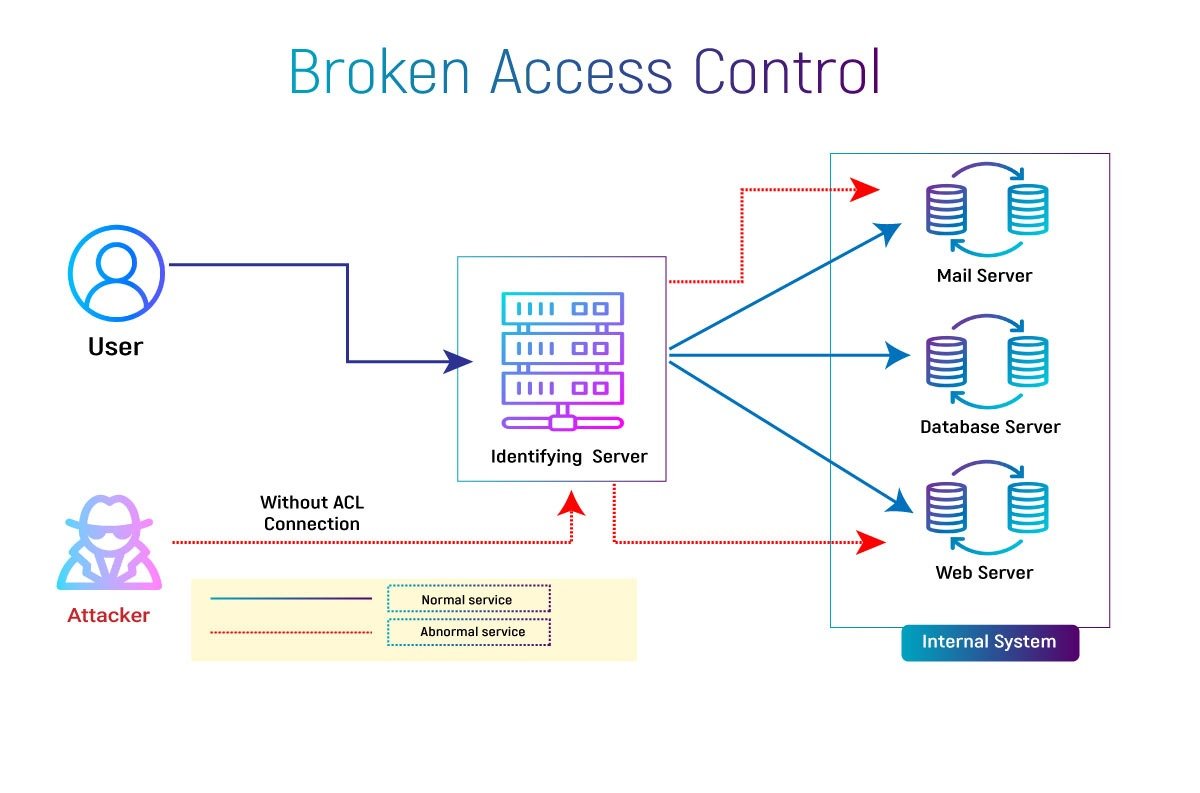
Consequences of Broken Access Control?
The repercussions of broken access control can be severe. For example, an attacker can gain access to sensitive data, modify or delete data, or perform unauthorized actions on behalf of legitimate users. This can lead to reputational damage, financial loss, and legal consequences.
Types of Broken Access Control?
One common type of broken access control is direct object reference. This occurs when a web application exposes a reference to an internal object, such as a file or database record, in a way that allows an attacker to manipulate the reference to gain unauthorized access. For example, a web application may use a parameter in the URL to point to a specific user account. If the application does not properly verify the user’s identity and privileges, an attacker could modify the parameter to gain access to another user’s account.
Another common type of broken access control is insecure direct object references. This occurs when a web application exposes a reference to an internal object in a predictable way, such as using sequential IDs. This allows an attacker to easily guess the references and gain unauthorized access. For example, a web application may use sequential IDs to reference files stored on a server. If the application does not properly validate the user’s identity and permissions, an attacker could guess the IDs and access files they should not have access to.
How can Broken Access Control attacks be prevented?
To hinder broken access control, web application developers must properly implement access control mechanisms. This includes using role-based access control, which grants or denies access based on a user’s role within the organization, and attribute-based access control, which grants or denies access based on specific attributes of the user or resource. Developers should also use secure coding practices, such as input validation and output encryption to prevent direct object references and insecure direct object references.
In addition, organizations should conduct regular security assessments of their web applications to identify and address potential vulnerabilities. This can include penetration testing, vulnerability scans, and code reviews.
Conclusion
In summary, broken access control is a critical issue that can compromise web application security. It occurs when web applications do not properly implement access control mechanisms and allow users to access resources they should not have access to. To prevent broken access control, web application developers must properly implement access control mechanisms and use secure coding practices. Organizations should also conduct regular security assessments to identify and address potential vulnerabilities. By taking these steps, organizations can improve the security of their web applications and protect against the consequences of broken access control.








