Broken authentication is a common security vulnerability that occurs when an attacker is able to compromise the authentication process used by a system.
Authentication is the process of verifying the identity of a user, and broken authentication can occur in various forms, such as weak passwords, flawed session management, and insufficient account lockout mechanisms.
Broken authentication attacks are common and can be devastating to an organization. They are also highly preventable.
Poor coding and logic errors in the authentication mechanism allow attackers to bypass the entire authentication process. This is exactly what “Broken Authentication” is.
You can help prevent broken authentication attacks by carefully deciding your default login credentials mode and make sure that after the initial setup, the default password is not used for further authentication.

This vulnerability can result in a variety of security risks, including data theft, unauthorized access to critical systems, and even complete system compromise.
In this blog, we will discuss what broken authentication is, how it works, and what steps you can take to prevent it.
What is Broken Authentication?
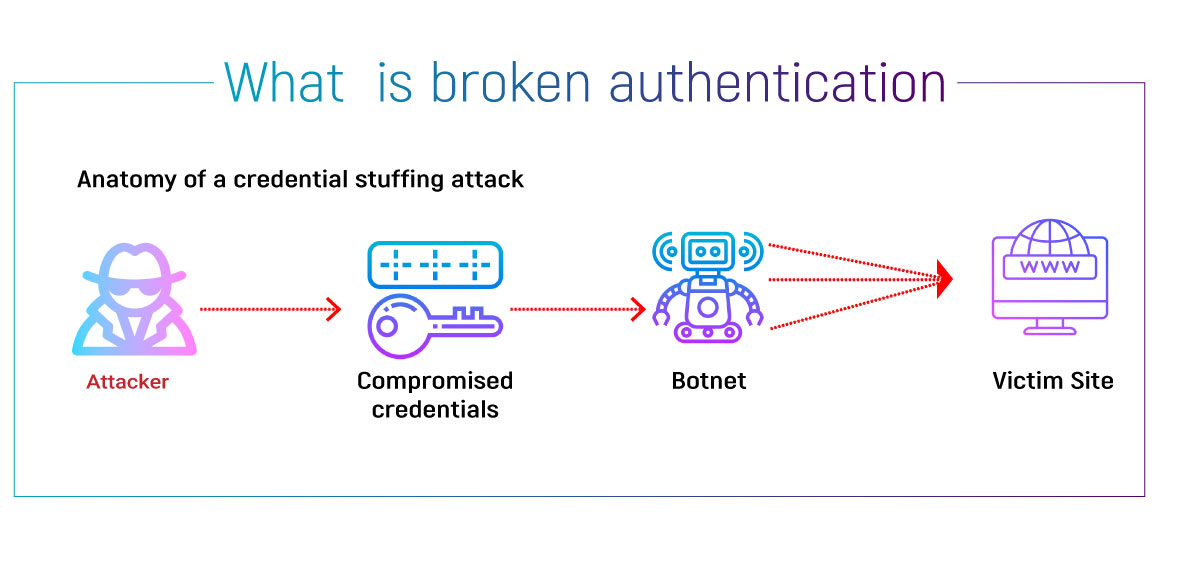
Authentication is the process of verifying the identity of a user or system. It typically involves providing a username and password or other credentials that are used to confirm that the user is who they claim to be. Broken authentication occurs when an attacker is able to exploit a weakness in the authentication mechanism to gain unauthorized access to the system or sensitive data.
How does Broken Authentication Work?
There are many ways in which an attacker can exploit a broken authentication vulnerability. One common method is to use brute force attacks to guess a user’s password. This involves using automated tools to try a large number of possible passwords until the correct one is found. Another method is to steal user credentials through phishing or other social engineering techniques. This can involve tricking users into providing their login credentials through fake login pages or other means.
Once an attacker has gained access to a user’s credentials, they can use them to access the system or data without further authentication. This can allow them to steal sensitive information, modify data, or even take control of the entire system.
How to Prevent Broken Authentication?
Preventing broken authentication requires a multi-layered approach that involves a combination of technical and procedural measures. Here are some of the key steps you can take to prevent broken authentication:
Use Strong Passwords:
One of the most effective ways to prevent brute force attacks is to use strong passwords that are difficult to guess. This means using a combination of upper- and lower-case letters, numbers, and symbols, and avoiding common words or phrases.
Implement Multi-Factor Authentication: Multi-factor authentication involves requiring users to provide more than one form of authentication before granting access to a system or data. This can include using a password plus a fingerprint or other biometric data, or using a token or smart card.
Educate Users:
One of the most common ways that attackers gain access to credentials is through social engineering attacks. Educating users on how to recognize and avoid these attacks can go a long way toward preventing broken authentication.
Limit Access:
Another way to prevent broken authentication is to limit access to sensitive systems and data to only those users who need it. This can involve implementing role-based access control, which grants users access based on their job responsibilities.
Keep Software Up to Date:
Many broken authentication vulnerabilities are caused by outdated software or configurations. Keeping software up to date and implementing security patches can help prevent these vulnerabilities from being exploited.
Conclusion
Broken authentication is a serious security vulnerability that can result in significant data breaches and system compromise. However, by implementing strong passwords, multi-factor authentication, user education, access controls, and software updates, you can significantly reduce the risk of this vulnerability. By staying vigilant and taking proactive steps to protect your systems and data, you can keep your organization safe from the risks of broken authentication.









