What is a Supply Chain Attack?
The supply chain includes everything from the delivery of materials from suppliers to manufacturers to delivery to end users. Supply chain attacks aim to exploit trust relationships between organizations and external parties. These relationships may include partnerships, vendor relationships, or use of the software by third parties.
Cybercriminals use supply chain attacks to manipulate a company’s manufacturing processes through hardware or software. Malware can be installed at any stage of the supply chain. This cyber-attack can also lead to disruption or failure of the company’s services. Supply chain attacks exploit trust relationships between different organizations. The attackers can target the weakest link in the supply chain of trust. Even if a company has strong cybersecurity, attackers will target trusted vendors if they are insecure. With a foothold in the provider’s network, this trust relationship allows the attacker to move to a more secure network.
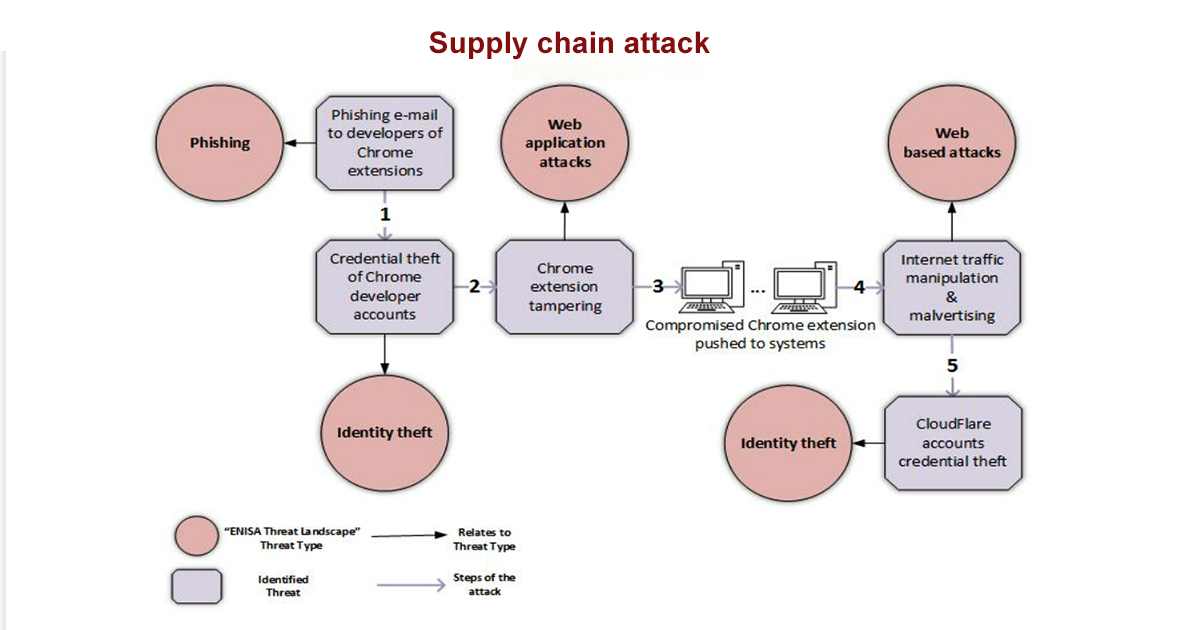
Supply chain attackers target the insecure vendors. If one organization has strong cybersecurity but has an insecure trusted vendor, then the attackers will target that vendor. MSPs are the most vulnerable to SCA because they have extensive access to customer networks that are irreplaceable to attackers. The biggest SCA in recent years are SolarWinds, Kaseya, Codecov, NotPetya, and Atlassian.
Best practices for identifying and mitigating Supply Chain Attacks include:
-
Follow DevSecOps practices
-
Perform network segmentation
-
Implement least privilege
-
Automated threat defense and threat hunting
Check Point helps organizations protect against these threats by monitoring applications for suspicious behavior that could indicate compromise. The impact of a supply chain attack simply provides another opportunity for attackers to breach an organization’s defenses. They can be used to carry out all kinds of cyber attacks, including data breaches and malware infections.
Attacks on the supply chain are becoming an increasingly business-critical problem, impacting critical relationships with partners and suppliers. Attacks on the supply chain are difficult to detect. Also, just because a software product has been validated in the past does not mean that the software is safe today. In addition to rigorously evaluating deployed vendors, organizations should mitigate the risk of their supply chain becoming vulnerable to attack. This requires the use of effective prevention, detection and response techniques.
Ways to protect from Supply Chain Attacks:
-
Can use strict code integrity policies to ensure that only authorized apps can run.
-
Use endpoint detection and response solutions.
-
Detection and solutions should automatically detect and remediate suspicious activity.
For software vendors and developers:
-
Keep a highly secure build and update infrastructure.
-
Apply OS and software security patches immediately.
-
Implement mandatory integrity controls to ensure only trusted tools are run.
-
Require multi-factor authentication for administrators.
Supply chain security is a top priority for companies, as a system breach can damage or disrupt operations. Vulnerabilities in the supply chain can lead to unnecessary costs, inefficient delivery times and loss of intellectual property.
All critical vendors must undergo a cybersecurity review as part of their organization’s vendor management program. Since an on-site visit may not be practical, you can look for independent audits performed to ensure the vendor adheres to cybersecurity best practices, including adopting Zero Trust capabilities. increase.
These delivery channels are responsible for most attacks, so vendors should pay particular attention to how they protect their endpoints from web-based malware and phishing. For example, if the original compromise was social engineering, remote browser isolation could have stopped the SolarWinds attack before it even started. Similarly, micro-segmentation could have stopped brute force attacks before the malware reached the Orion monitoring platform. Finally, adopting a zero trust approach based on the assumption that a breach will occur helps limit damage to your network and data if one of your providers is compromised. For example, implementing least-privilege access and micro-segmentation can limit provider access to minimize the damage that can occur in the event of a breach.









