What is a Cloud Access Security Brokers (CASB)?
CASB is the acronym for Cloud Access Security Brokers. A CASB is a cloud-based or on-premise security application positioned between users and cloud services. It is mainly used to manage and protect data in the cloud. CASB systems are half filter, half proxy and half firewall between users and cloud systems. They cannot provide complete functionalities of a filter, proxy and firewall. They have the capability to detect the access of unauthorized cloud applications and also can detect sensitive data in transit.
CASB solutions are not complete data security systems, as they provide security to some cloud specific applications only. Some general security features included in CASB solutions are : Authentication, Authorization, SSO (Single Sign On), Credential mapping, Device profiling, Encryption and tokenization, Logging and alerting, Malware detection and prevention etc. These security features may vary according to each CASB solution. Organizations should choose the CASB solution based on their specific use cases and functionalities available in each solution. For example: If an organization uses Salesforce, they will need a CASB solution that supports Salesforce APIs or has functionality designed to protect Salesforce traffic. Some popular CASB solutions are: Forcepoint, Lookout, McAfee, Microsoft, Netskope, Palo Alto Networks, Proofpoint.
Pillars of Cloud Access Security Brokers CASB)
Visibility
CASB solutions provide visibility to the organization about the traffic with cloud providers. CASB helps to see the sanctioned and unsanctioned applications accessed by the users.
Compliance
CASB solutions has the ability to classify the data passing through it, which can support the Compliance process.
Data Security
Most of the CASB solutions have the capability to detect sensitive data, encrypt or tokenize data, and control access to data, thus providing data security.
Threat Detection
CASB solutions have User Entity Behavior Analytical (UEBA) capability to detect insider threats and to identify compromised accounts. It can also scan the network to identify threats affecting the data.
CASB Deployments
A CASB can be deployed either on premises or in the cloud. Most of the CASB deployments are SaaS-based. There are mainly three types of CASB deployments.
API-Based
CASB will be placed in between the users and cloud platforms. APIs will receive all the traffic and apply appropriate security policies to these traffic.
Forward Proxy
The forward proxy will be positioned closer to the users and it can proxy traffic to multiple cloud providers. The CASB inspects the traffic from the users based on the predefined rules. CASB acts like a man-in-the-middle technique to pass the traffic from the users to cloud providers. The disadvantage of CASB as forward proxy is that each device accessing the proxy requires the installation of self-signed certificates, and an excess of users can cause latency.
Reverse Proxy
A reverse proxy will be positioned closer to the cloud application. Reverse proxies receive requests from the cloud application, apply predefined security rules, and pass the user’s request.
Prophaze WAF and CASB Integration
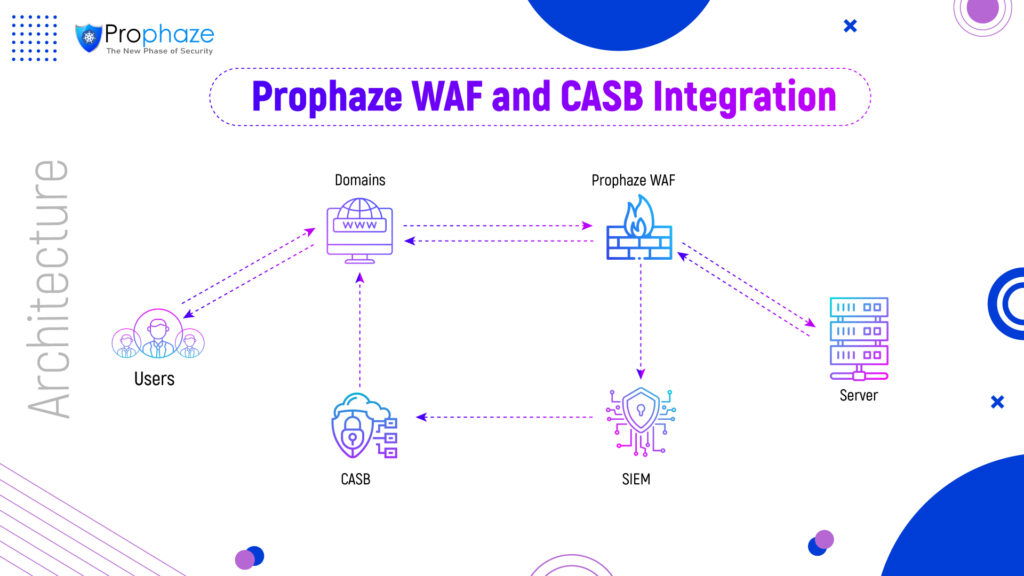
The above architecture shows the integration of Prophaze WAF and CASB solution. In this integration, there will be mainly two types of filtration – by the WAF and by the CASB. When users access the domains, all traffic will be passed through Prophaze WAF. The WAF will analyze the traffic and filter them into legitimate traffic and malicious traffic. Based on the build-in rules in the WAF, it allows the users to access only the legitimate traffic. Prophaze WAF protects the domains from all the known and unknown vulnerabilities and DDOS based on WAF Rules and AI/ML features. The logs from the WAF will be sent to the SIEM solution and the CASB solution gets the logs from the SIEM for further analysis.
CASB provides additional features for security based on cloud specific applications. At the CASB, again some more filtering occurs and based on the rules set in CASB, it can allow/block these traffic again. Thus, CASB allows only the allowed traffic to be accessed by the users. This integration is a value addition to both WAF and CASB solutions and provides two layers of security for applications.