A vulnerability scanner is a program that searches for vulnerabilities on a network, analyzing the attack surface. This software is very intrusive in the target code, causing reboots, errors, and decreased productivity. Vulnerability scanners are also great for discovering password breaches. But how do they work? What are the advantages and disadvantages of using them? Before getting into the details regarding vulnerability scanners, let’s discuss first about vulnerabilities.
What Are Vulnerabilities?
Vulnerabilities turn out to be weaknesses in software and hardware that can allow hackers to take control of your computer. They can sneak into your system during an update or even in the base code without you knowing. Older software systems often have these types of vulnerabilities, and they can be dangerous, too. Vulnerabilities can also be caused by human error. People can create them when they configure their hardware, email accounts, and social media privacy settings. Certain behaviors can also create vulnerabilities, such as downloading files from dubious sources. These behaviors are all opportunities for hackers to take advantage of your network and your data.
A vulnerability is an opening in software or hardware that hackers can exploit. A hacker could use this weakness to gain unauthorized access to your system. There are several levels of severity. A vulnerability may be as simple as an error in software code or as severe as compromising customer data. The best way to protect your website is to identify vulnerabilities through vulnerability scanners.
Here’s How Vulnerability Scanners Work?
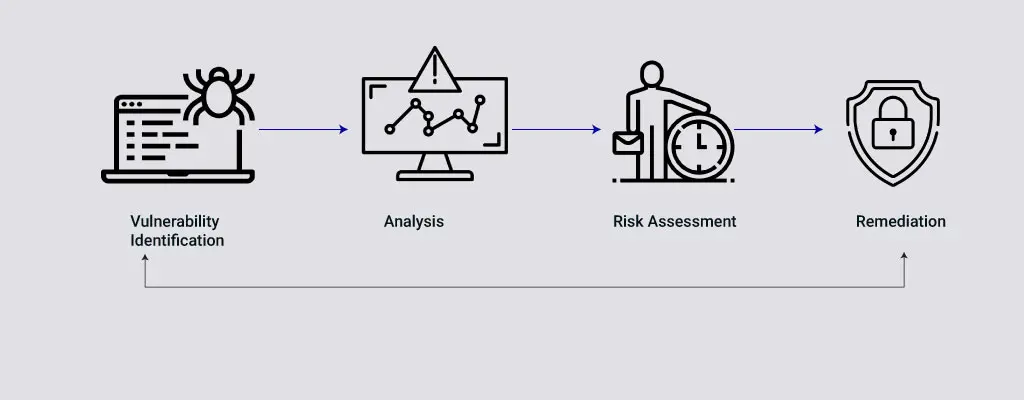
A vulnerability scanner works by running a scan on all of the devices within its scope of engagement. The outcome of this scan is then compared to a database of pre-existing vulnerabilities. This info is useful for identifying opportunities to improve security posture. Some vulnerability scanners can also be rerun automatically based on a schedule. But these network security tools are not always sufficient. They often require multiple tools, putting a strain on the network.
Vulnerability scanners identify vulnerabilities and display a report so that the user can fix them themselves. The latter, on the other hand, tries to exploit the vulnerability. Neither of these approaches is ideal. A vulnerability scanner can detect vulnerabilities on a network, but a good tool will also detect potential vulnerabilities on a system and provide recommendations. So, if you want to use a vulnerability scanner to improve your security, make sure you choose one with a powerful feature set.
Once you’ve sorted out which vulnerability scans are most important, vulnerability management software will provide recommendations for remediation. Sometimes, these recommendations are not the best option, but they can be a great start for reducing your risk. The remediation process can range from a simple software patch to replacing an entire fleet of physical servers. Then, you can repeat the vulnerability scan to ensure that you’ve patched all of the necessary systems.
A vulnerability scanner can identify both privileged and unprivileged networks. It can even find unauthorized services that are running on your network. Some scanners use privileged credentials to attack your organization. The vulnerability scanner uses a reference database of known bugs and flaws that can make your network vulnerable. This database is constantly updated as new vulnerabilities are introduced as a result of system changes.
Different Types of Vulnerability Scanners

Network Vulnerability Scanner
A network vulnerability scanner is a software tool used to detect security flaws in network infrastructures. A good one will scan for vulnerabilities on an ongoing basis, alerting you to any network changes and automatically updating its database. These scanners are generally reliable and scalable and should not negatively impact the performance of your network or impacted devices. Some scanners can even run on a schedule so that you don’t have to worry about wasting time checking them every day. They should also be easy to use and understand, as well as allow you to set up automatic scans and alerts.
The purpose of a network vulnerability scanner is to identify weaknesses in your network, so you can take appropriate action to mitigate them. The tools typically come with automated remediation tools. Some vulnerability scanners also offer compliance reports and other custom report formats. As a final note, a network vulnerability scanner is only one source of information and can’t replace knowledgeable employees. Hence, you must choose a network vulnerability scanner that fits your needs. This tool will assist you in determining which vulnerability to address first.
Web Application Vulnerability Scanner
Web application vulnerability scanners include dynamic application security testing, static application vulnerability scanning, and so on. Dynamic application security testing involves performing non-functional testing on an application to find any weaknesses and vulnerabilities. Some web application vulnerability scanners can be configured to scan other network devices, including printers, VoIP phones, and wireless access points. Firewalls can also prevent scanning scans, so be sure to check whether they allow it before installing a web application vulnerability scanner. Using a web application vulnerability scanner can help you detect and prevent vulnerabilities, so be sure to use one that has a high level of integration with other security tools.
A web application vulnerability scanner should be able to detect vulnerabilities hidden behind the login page, which are often the most common entry points for attackers. It should be able to detect any vulnerabilities hidden behind login pages, such as adding, editing, and deleting data, uploading files, and interfacing with other users. Authenticated web application scanning can be beneficial for businesses where some critical functionality lies behind login pages. This means that a significant percentage of the attack surface can be hidden behind the login page. So, ensure that the scanner you use functions in a way to detect such threats.
Open-Source Vulnerability Scanner
An open-source vulnerability scanner can help you identify open-source packages that may have legal restrictions or require you to pay a fee to use them. Depending on the license terms, these open-source packages may contain certain restrictions, like granting attribution for modifications or allowing only certain users to use them. Open-source vulnerability scanners will make this process easier for you. An open-source vulnerability scanner will help you to identify vulnerabilities and fix them before attackers can use them to attack your network. It is extremely easygoing to use and configure, allowing you to scan individual assets, groups of assets, or even your entire network. Moreover, you can schedule scans and set the level of threat to prioritize responses.
The first step to visibility is knowing the pedigree and background of open source components. An open-source vulnerability scanner can review the dependencies and code repositories to establish an inventory of open-source components. They also identify relevant metadata and software licenses. This inventory helps you check for conflicts with organization policies. Before choosing this scanner, ensure that it aligns with your organization’s open source licenses and policies.
The Takeaway: Choose What’s Right for You!
Before purchasing a vulnerability scanner, it’s important to understand its capabilities and limitations. Focus on the fact that the scanner is comprehensive and effectively scans key IT assets, including database servers and business-critical services. You should also consider your company’s unique situation while choosing a scanner. Once you are done with these, ensure that the scanner must be able to probe underneath layers of protection and identify any vulnerabilities.
If you’re looking for any assistance regarding the same, reach out to Prophaze.












