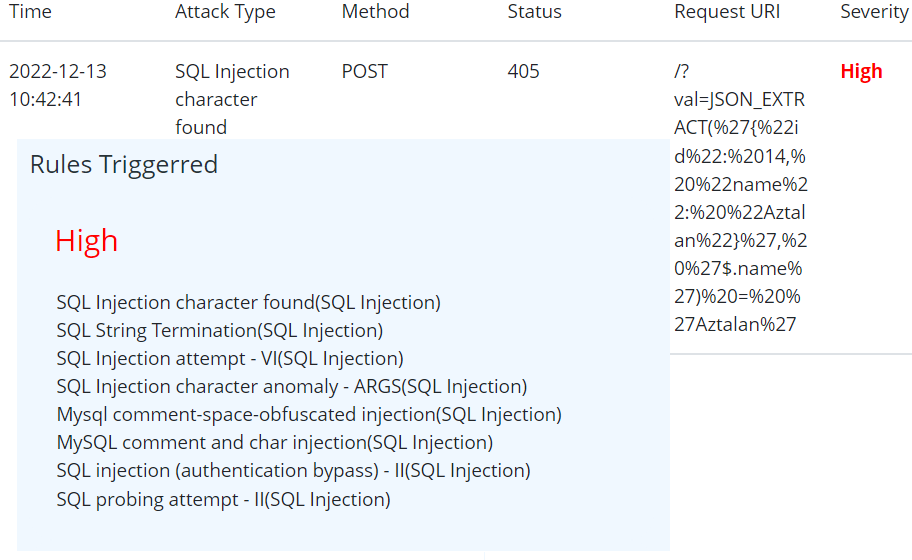
Json – SQL WAF Bypass Mitigation
A New WAF Bypass hack has been identified by claroty team. This uses json based sql strings which is not conventionally been
Website Security using Web Application Firewall – Prophaze WAF

A New WAF Bypass hack has been identified by claroty team. This uses json based sql strings which is not conventionally been
The Prophaze Cloud WAF is built natively on the Kubernetes Platform and protects clients’ Kubernetes clusters and cloud infrastructure from

Prophaze WAF can protect Java-based Applications that are prone to recent log4j vulnerability. Prophaze is pre-equipped with live signatures of

In a time of rising cyber threats, a WAF for financial services and fintech projects is essential for ensuring that

A WAF is an essential component of any modern data security solution for the food industry. This tool helps protect

The Firewall Web Application (WAF) is an important component of your web security strategy. Unlike traditional security technologies, it is

The Internet has become a highway to reach the global consumer list within a few clicks. But this advancement can

In order to use WAF in Docker containers, you need to create a persistent volume. Then, create a folder called

A web application firewall for startups is vital to keeping data safe. Even the smallest teams can be vulnerable to

Web applications form a massive part of the common network ground that is shared by a business and its customers

Everyone knowing about OWASP must be curious about what’s modified withinside the Top 10 for 2021. Here’s What’s New in

A cloud WAF is also known as a cloud-based WAF or cloud-native WAF and it provides web application security more

Application security is the method that is used to secure web apps. In this we find, fix and enhance the

A web application firewall (WAF) secures a web application such as websites from several application attacks such as cross-site scripting

Cyber breaches have always been a concern for businesses across all industries. Their after-effects lead to compromised customer loyalty &

Cloud computing mainly aims at providing fast, easy-to-use computing and data storage services at a low cost. Cloud environment does

Since COVID-19 has hit the world with its wrath, the business world has turned upside down, companies are shifting to

The universe is full of secrets and almost everything surrounding you has tons of secrets just waiting to be discovered.

The cloud market has seen an exponential increase in 2020 and this trend was observed amid the steepest economic contraction

The core to any container security effort is testing the code and supplementary components which will execute within containers, and

The process of creating an accurate virtual patch is bound by: (a) No false positives – This is always the

Preparation Phase The significance of adequately utilizing the preparation phase in respect of virtual patching can’t be overstated. Before dealing with a discovered vulnerability,

There are many products out there that work as a WAF. WAF is not really aware of the application it

Patch Management is a strategic process of acquiring, testing, and installing updated software. But, most of the companies find themselves