Private Cloud Firewall
Private Cloud Infrastructure with Prophaze
Prophaze virtual firewalls protect your applications and data in the private cloud, well-defined software networks, and virtual data centers. Provides consistent policies across central management through deep visibility, and cloud environment. Prophaze provides several security products by combining firewalls, VPNs, access control, and IPS technologies, to improve security posture and defend against potential threats in order to address this issue.
Advance Protection for Your Private Cloud Security !
Streamlining Security and Scalability
The trending deployment platform for private cloud is Kubernetes, where Prophaze can be installed as a microservice within the existing k8 cluster, functioning as an ingress controller.
Setting up the endpoint IP addresses in the Prophaze Dashboard, configuring the domain DNS to point to the WAF, and installing Prophaze behind the load balancer are all steps in setting up the Prophaze as a virtual WAF server in a private cloud account. You also stress the significance of defining the host specifications depending on the anticipated bandwidth for the best deployment. Good work!
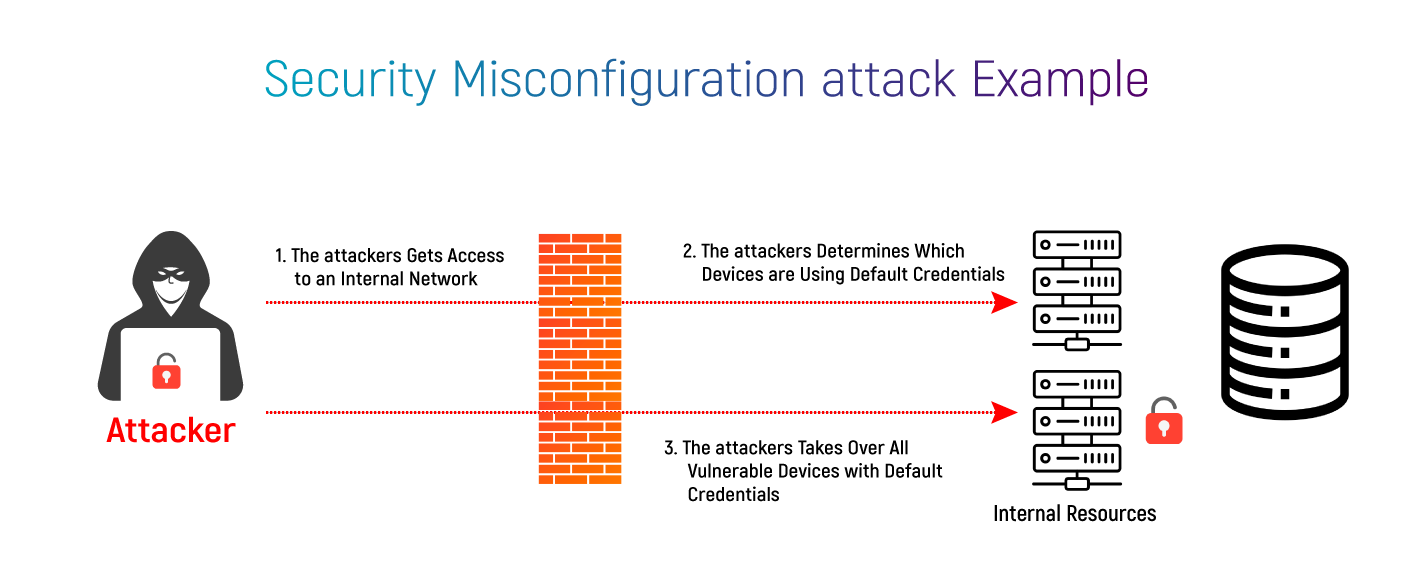
Protection and Control on Private Cloud Environment
Prophaze is designed for public cloud environments based on-premises and can be integrated with cloud services such as AWS, Azure, and GCP to enhance security and control over traffic.
Prophaze’s On-premises WAFs are placed near the application to scrutinize inbound and outbound traffic equally, ensuring that traffic remains within the cluster and stays protected. Prophaze is deployed as a DNS-level reverse proxy to secure all traffic entering the cluster’s services. Overall, Prophaze’s deployment model provides a strong and dependable solution for safeguarding public cloud environments.
