Automated threats identified by the OWASP organization are malicious activities performed by automated tools. Account aggregation is one such automated threat that can pose a significant risk to web application security. In this article, we will discuss what account aggregation is and how it can be prevented.
What is Account Aggregation?
Account aggregation is a malicious activity where automated tools are used to gather a user’s account information from multiple sources and compile it into a single view. This process is often done through a web application that connects to the user’s financial accounts. Once the automated tools have access to the user’s financial information, they can potentially steal sensitive data, leading to significant financial losses and damage to a user’s credit score.
Automated tools used for account aggregation are often referred to as account checkers. These tools are designed to test a large number of login credentials against multiple websites to gather account information. Account checkers use various techniques to automate the process of testing login credentials, such as using a list of common passwords and usernames, or brute-force attacks. Once account checkers have access to a user’s financial information, they can potentially steal sensitive data and cause significant financial losses. As a result, it is crucial for web application developers to take appropriate measures to prevent account checkers from accessing users’ accounts and stealing sensitive data.
Preventing Account Aggregation
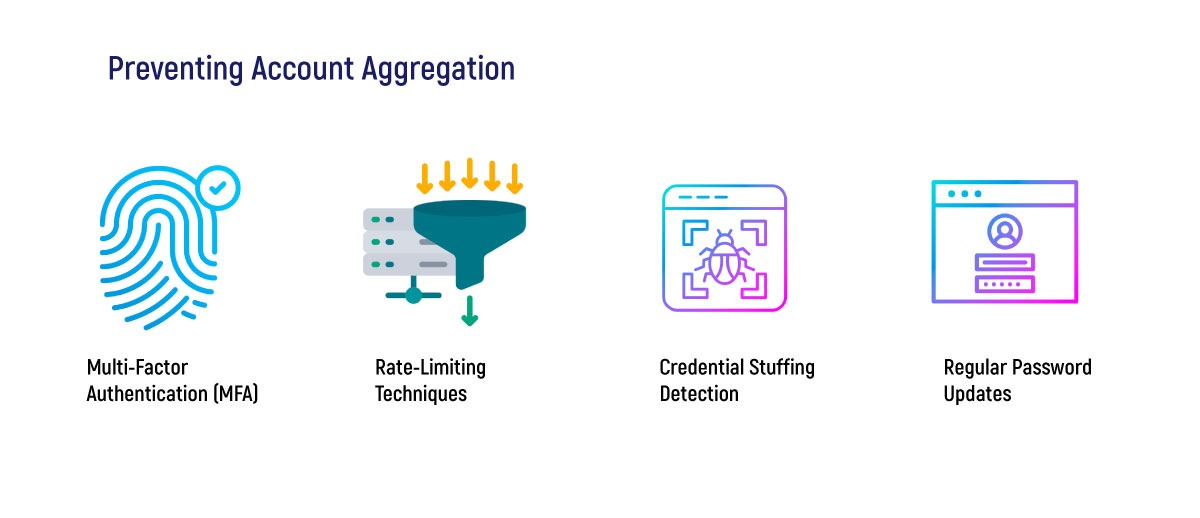
To prevent these kind of threats, web application developers can implement various security measures such as –
Multi-Factor Authentication (MFA):
Implementing MFA requires users to provide multiple forms of identification before accessing their accounts, making it more challenging for automated tools to gain access. MFA can involve the use of biometric verification, SMS authentication, or a security token that is not tied to the user’s computer or phone.
Rate-Limiting Techniques:
Rate-limiting techniques can be used to prevent automated tools from attempting multiple login attempts in a short period. Developers can restrict login attempts, require users to answer security questions after a certain number of login attempts, or implement CAPTCHA checks to prevent bots from accessing the login page.
Credential stuffing detection:
It is important to detect and block automated tools that try to use stolen credentials. Credential stuffing detection techniques can monitor login attempts and check for patterns that suggest automated tools are being used.
Regular Password Updates:
Users should be encouraged to update their passwords regularly and use strong, unique passwords. This will make it harder for attackers to gain access to accounts even if they do obtain login credentials through other means.
Conclusion
Account aggregation is a significant risk to web application security, and web application developers must take appropriate measures to curb it. By implementing security measures such as multi-factor authentication, rate-limiting techniques, etc., developers can prevent automated tools from gaining access to users’ financial information. By taking this multi-faceted measure, it is essential to prioritize web application security to protect users’ sensitive data and prevent financial losses.