Kubernetes Security: Build Phase
Overview : Kubernetes Security: Build Phase Securing containers and Kubernetes starts within the building part with securing your container images.
Overview : Kubernetes Security: Build Phase Securing containers and Kubernetes starts within the building part with securing your container images.

Overview : DoS vulnerability in the file upload request feature of Atlassian Crucible Affected Product(s) : version < 4.7.4 4.8.0
Overview : Around 87% of organizations are using Kubernetes container orchestration to manage their container workloads. Each of the security
Overview : Kubernetes helps the enterprises to automate their application deployment for the business benefits. Now-a-days Kubernetes security can be

Overview : HCL BigFix Inventory does not enforce “secure” attribute for SSO related cookies when SSO is enabled. Web browsers

Overview : Online Bus Ticket Reservation 1.0 – SQL Injection Affected Product(s) : Version: 1.0 Vulnerability Details : CVE ID

Overview : Multiple vulnerabilities reported in BIG-IP Traffic Management User Interface Affected Product(s) : BIG-IP versions 16.0.0 – 16.0.0.1 BIG-IP

Overview : XSS issue in Gitlab CE/EE Affected Product(s) : from 12.4 before 13.4.7, 13.5 before 13.5.5, and 13.6 before

Overview : Multiple vulnerabilities reported in AEM’s Cloud Service offering Affected Product(s) : AEM Forms SP6 add-on for AEM 6.5.6.0

Overview : XSS issue in WebUI Translation in Systran Pure Neural Server Affected Product(s) : Systran Pure Neural Server before

Overview : Access controls vulnerabilities in containerd containers Affected Product(s) : containerd v1.4.2 containerd v1.3.8 Vulnerability Details : CVE ID

Overview : Privilege issues in Kubernetes kube-apiserver Affected Product(s) : kube-apiserver v1.18.0-1.18.5 kube-apiserver v1.17.0-1.17.8 kube-apiserver v1.16.0-1.16.12 all kube-apiserver versions prior

Overview : CSV injection in netskope Admin UI (Version 75.0) Affected Product(s) : Netskope 75.0 Vulnerability Details : CVE ID
Cyber landscape predictions FireEye Mandiant has delivered its cyber landscape predictions for the coming year, including growing and affiliate-supported espionage,

Overview : Multiple vulnerabilities reported in Nextcloud Affected Product(s) : Nextcloud Social app version 0.3.1 Nextcloud Social < 0.4.0 Vulnerability
Overview : Multiple vulnerabilities reported in GitLab EE Affected Product(s) : Affected versions are >=10.2, <13.3.9,>=13.4, <13.4.5,>=13.5, <13.5.2. Affected versions

Overview : Kaa IoT Platform version 1.2.0 suffers from a persistent cross site scripting vulnerability. Affected Product(s) : Kaa IoT
Overview : Permissions missuses in Nagios Affected Product(s) : Nagios XI 5.7.4 Vulnerability Details : CVE ID : CVE-2020-5796 Improper

Overview : Remote Code Execution in CMSUno 1.6.2 Affected Product(s) : Version: 1.6.2 Vulnerability Details : CVE ID : CVE-2020-25538
Overview : Cross-Site Scripting (XSS) vulnerability on API Manager 3.1.0 Affected Product(s) : WSO2 API Manager Vulnerability Details : CVE
Prototype Pollution Prototype Pollution is a vulnerability affecting JavaScript. Prototype Pollution refers to the ability to inject properties into existing
CVE-2019-20901 Proof of Concept : The login.jsp resource in Jira before version 8.5.2, and from version 8.6.0 before version
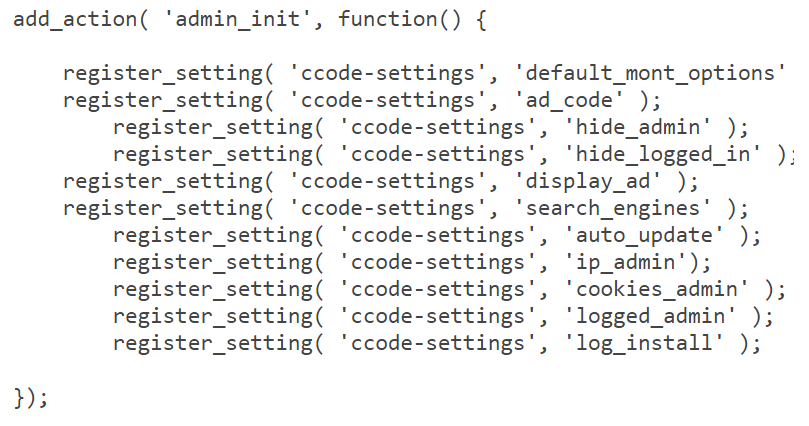
A new variant of popup injector WordPress malware is spreading and affecting 1000s of WordPress websites. The web master was

Overview : nghttpd is a multi-threaded static web server. nghttpd only accepts HTTP/2 connections via NPN/ALPN or direct HTTP/2 connections.