prophaze-vs-imperva
Prophaze vs Imperva A Comprehensive Comparison At Prophaze, we understand the critical importance of safeguarding your digital assets from evolving
Prophaze vs Imperva A Comprehensive Comparison At Prophaze, we understand the critical importance of safeguarding your digital assets from evolving
Prophaze vs Azure A Comprehensive Comparison At Prophaze, we understand the critical importance of safeguarding your digital assets from evolving
Prophaze vs AWS A Comprehensive Comparison At Prophaze, we understand the critical importance of safeguarding your digital assets from evolving
Prophaze vs Cloud Armor A Comprehensive Comparison At Prophaze, we understand the critical importance of safeguarding your digital assets from

In an ever-evolving cybersecurity threat, APT29, also known as Cozy Bear, is a dangerous state-sponsored cyber-espionage network linked to the
Prophaze vs Cloudflare A Comprehensive Comparison At Prophaze, we understand the critical importance of safeguarding your digital assets from evolving

A recent study conducted by an IIT Kanpur-incubated start-up revealed alarming statistics, revealing that financial frauds accounted for a staggering

Generic Routing Encapsulation (GRE) is a tunneling protocol that encapsulates various network protocols within Internet Protocol (IP) packets. User Datagram

When it comes to maintaining your online presence and increasing website performance, you need a robust WAF (Web Application Firewall)

The Character Generator (CharGEN) protocol was originally designed for testing and debugging purposes. It allows a client to request a
Attacks on Application Programming Interfaces (APIs) have become significant cybersecurity challenges in today’s digital landscape. Bot attacks on APIs involve

What Are The Deployment Options For A WAF? Discover the deployment options for a Web Application Firewall (WAF) and choose

Token cracking is a type of OWASP-identified automated threat that involves an attacker attempting to guess or crack access tokens

Description Generex UPS CS141 below 2.06 version, could allow a remote attacker to upload a firmware file containing a webshell

Description InHand Networks InRouter 302, prior to version IR302 V3.5.56, and InRouter 615, prior to version InRouter6XX-S-V2.3.0.r5542, contain vulnerability CWE-284:

Description The bootloader in the Nokia ASIK AirScale system module (versions 474021A.101 and 474021A.102) loads public keys for firmware verification

Description Certain General Electric Renewable Energy products have a hidden feature for unauthenticated remote access to the device configuration shell.

Description Dataprobe iBoot-PDU FW versions prior to 1.42.06162022 contain a vulnerability where a specific function does not sanitize the input
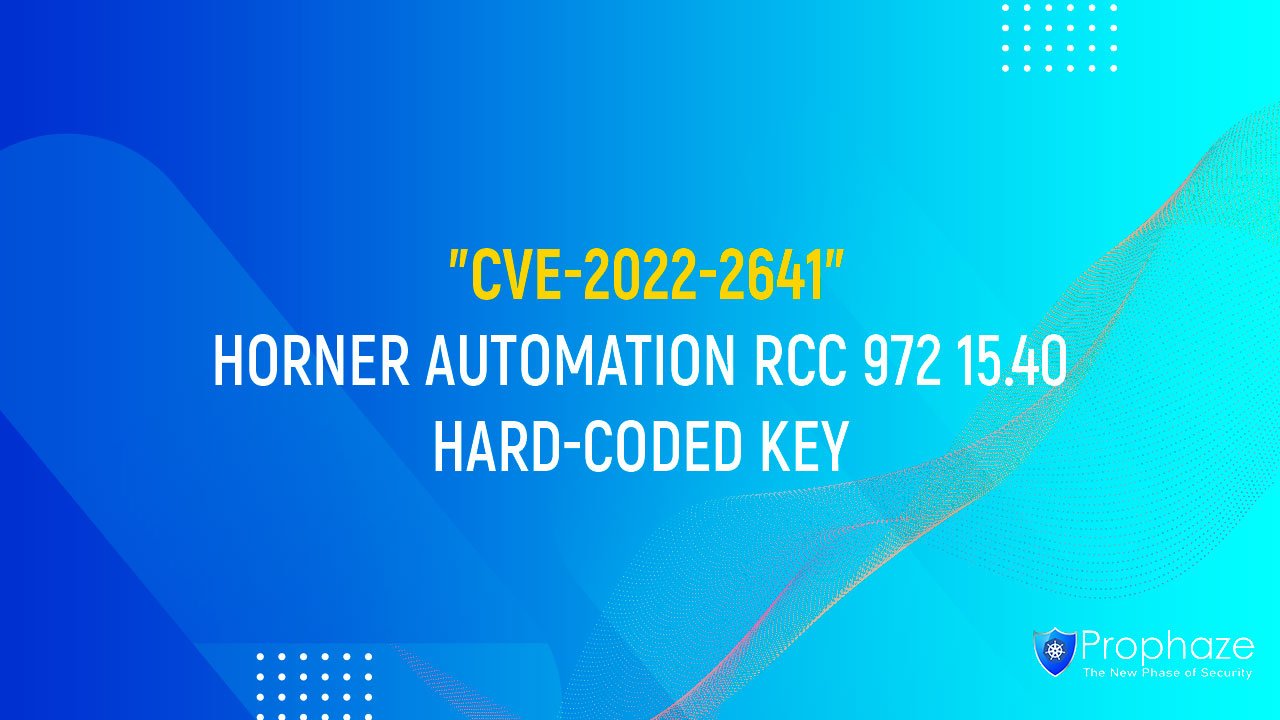
Description Horner Automation’s RCC 972 with firmware version 15.40 has a static encryption key on the device. This could allow
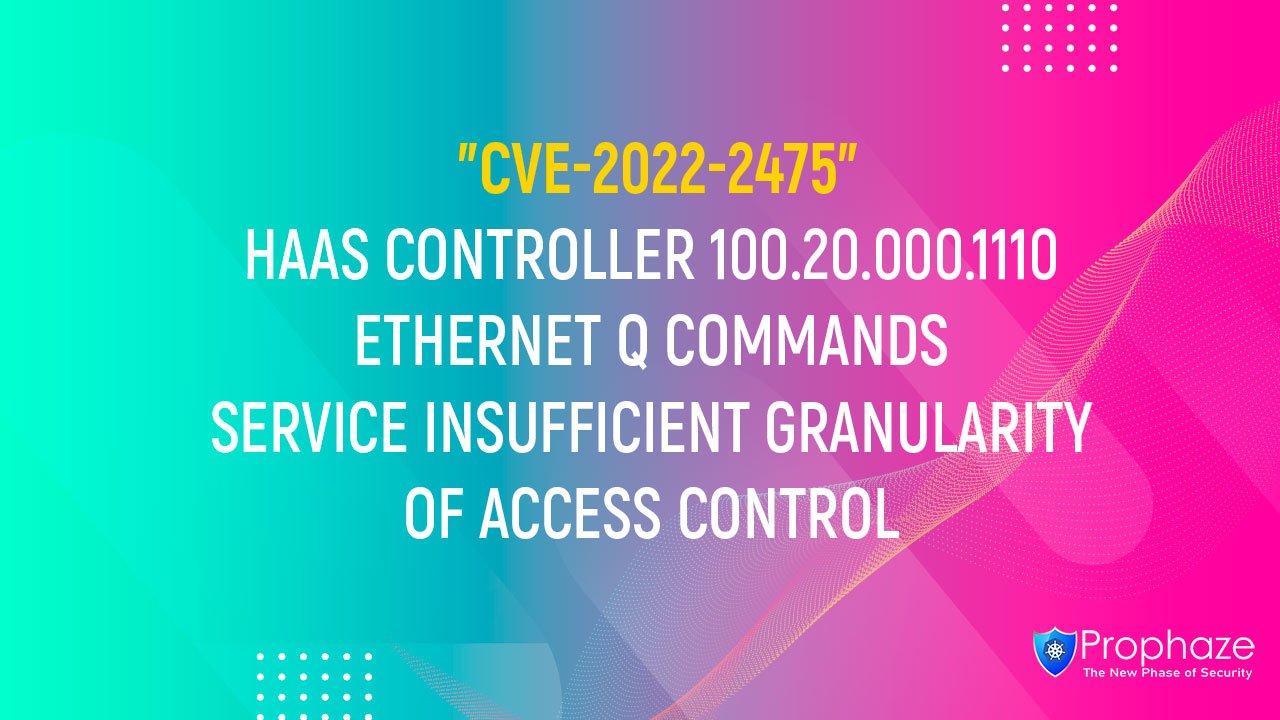
Description Haas Controller version 100.20.000.1110 has insufficient granularity of access control when using the “Ethernet Q Commands” service. Any user

Description All versions of iSTAR Ultra prior to version 6.8.9.CU01are vulnerable to a command injection that could allow an unauthenticated
Home Cloud Our Cloud Server span around the globe which only required dns change for application onboarding. PROPHAZE APPSEC PLATFORM

Secure Access Service Edge (SASE) Tools are the network architecture framework that brings together the cloud native security technologies along
Cloudflare Pro Prophaze Explorer Fast, easy-to-use DNS DNS is changed at Existing DNS Manager (Fast Propagation) Free automated SSL certificates