Tracking Changes Made from 2007 to 2013 Reports
OWASP analyses the most crucial web application security flaws. OWASP being a vendor-independent, non-profit IT security organization, refreshes the list of Top 10 web application security flaws once at regular intervals of three years as IT security dangers increase and evolve with time.
OWASP has been under-functioning since 2001. The first OWASP report was published on 2003. We have fetched reports from the year 2007 till now. Let’s check the prominent changes introduced along with images to understand the list of attacks and work performed by OWASP.
OWASP Top 10: 2010 Edition in Comparison with 2007 Edition
Image Source: https://owasp.org/www-pdf-archive//OWASP_AppSec_Research_2010_OWASP_Top_10_by_Wichers.pdf
Major Changes Introduced from 2007 to 2010
It’s Related to Risks, Not Vulnerabilities.
- New title: “The Top 10 Most Critical Web Application Security Risks” OWASP Top 10 Risk Rating Methodology.
Depending on the OWASP Risk Rating Methodology
- Used to focus on Top 10.
2 Risks Added, 2 Dropped
- Added A6: Security Misconfiguration.
It was A10 in 2004 Top 10 List: Insecure Configuration Management.
- Added A10: Invalidated Redirects and Forwards
Relatively normal and VERY dangerous flaw that isn’t notable
- Removed A3: Malicious File Execution
Primarily a PHP flaw that is getting dropped in prevalence.
- Removed A6: Information Leakage & Improper Error Handling
An extremely prevalent flaw that doesn’t introduce a lot of risks (normally)
OWASP Top 10: 2013 Edition in Comparison with 2010 Edition
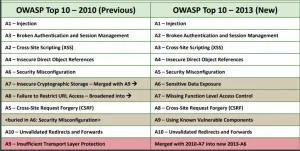
Image Source: https://owasp.org/www-pdf-archive/OWASP_Top_10_-_2013.pdf
Major Changes Introduced from 2010 to 2013
The danger landscape for applications security continually changes. Key factors in this development are made by aggressors, the arrival of new innovations with new shortcomings just as more implicit guards, and the sending of progressively complex frameworks. To keep pace, we occasionally update the OWASP Top 10. In this 2013 delivery, we rolled out the accompanying improvements:
- Broken Authentication and Session Management climbed in commonness dependent on our data set. We accept this is most likely on the grounds that this region is being taken a gander at harder, not on the grounds that these issues are, in reality, more predominant. This made Risks A2 and A3 switch places.
- Cross-Site Request Forgery (CSRF) dropped down in predominance dependent on our data set from 2010-A5 to 2013-A8. We accept this is on the grounds that CSRF has been in the OWASP Top 10 for a very long time, and associations and system engineers have zeroed in on it enough to essentially decrease the quantity of CSRF weaknesses in genuine applications.
- We widened Failure to Restrict URL Access from the 2010 OWASP Top 10 to be more comprehensive:
Added:
2010-A8: Failure to Restrict URL Access is currently 2013-A7: Missing Function Level Access Control – to cover all of function level access control. There are numerous ways of determining what function is being accessed, in addition to the URL.
- We blended and widened 2010-A7 and 2010-A9 to CREATE: 2013-A6: Sensitive Data Exposure:
Removed:
This new class was made by combining 2010-A7 – Insecure Cryptographic Storage and 2010-A9 – Insufficient Transport Layer Protection, in addition to adding program side sensitive data hazards also. This new class covers sensitive data insurance (other than access control which is covered by 2013-A4 and 2013-A7) from the second sensitive data is given by the client, shipped off and put away inside the application, and then, at that point, sent back to the program once more.
- We added: 2013-A9: Using Known Vulnerable Components:
Added:
This issue was referenced as a feature of 2010-A6 – Security Misconfiguration; however, it presently has its very own classification as the development and profundity of part-based advancement has fundamentally expanded the danger of utilizing known weak parts.












