What is Session Hijacking?
Session Hijacking is the type of attack in which the attacker takes over or hijacks a user’s session and exploits other attacks through that hijacked session. Session Hijacking can be done by obtaining the user’s session ID or session token. Session hijacking can be either active or passive. In active session hijacking, the attack is performed when the victim’s session is still active. In passive session hijacking, the attack can be performed even if the victim’s session is not active at the time of attack, using the user session tokens which was obtained by the attacker earlier.
Different types of Session Hijacking techniques:
Predicting Session tokens
When the servers use some custom algorithm to generate session tokens, then by analyzing the pattern of session tokens, the attacker can predict a valid session ID to gain access.
IP spoofing
IP spoofing means acting like a legitimate user, using that user’s IP. In this technique, the attacker injects his own packets, spoofed with the IP address of the client into the TCP session of the client and server communication and acts itself as an authenticated user to gain unauthorized access.
Man-in-the-middle attack
In this technique, the attacker uses a sniffer, in which the attacker observes the communication between client and server and collect the user data and user this data to gain unauthorized access.
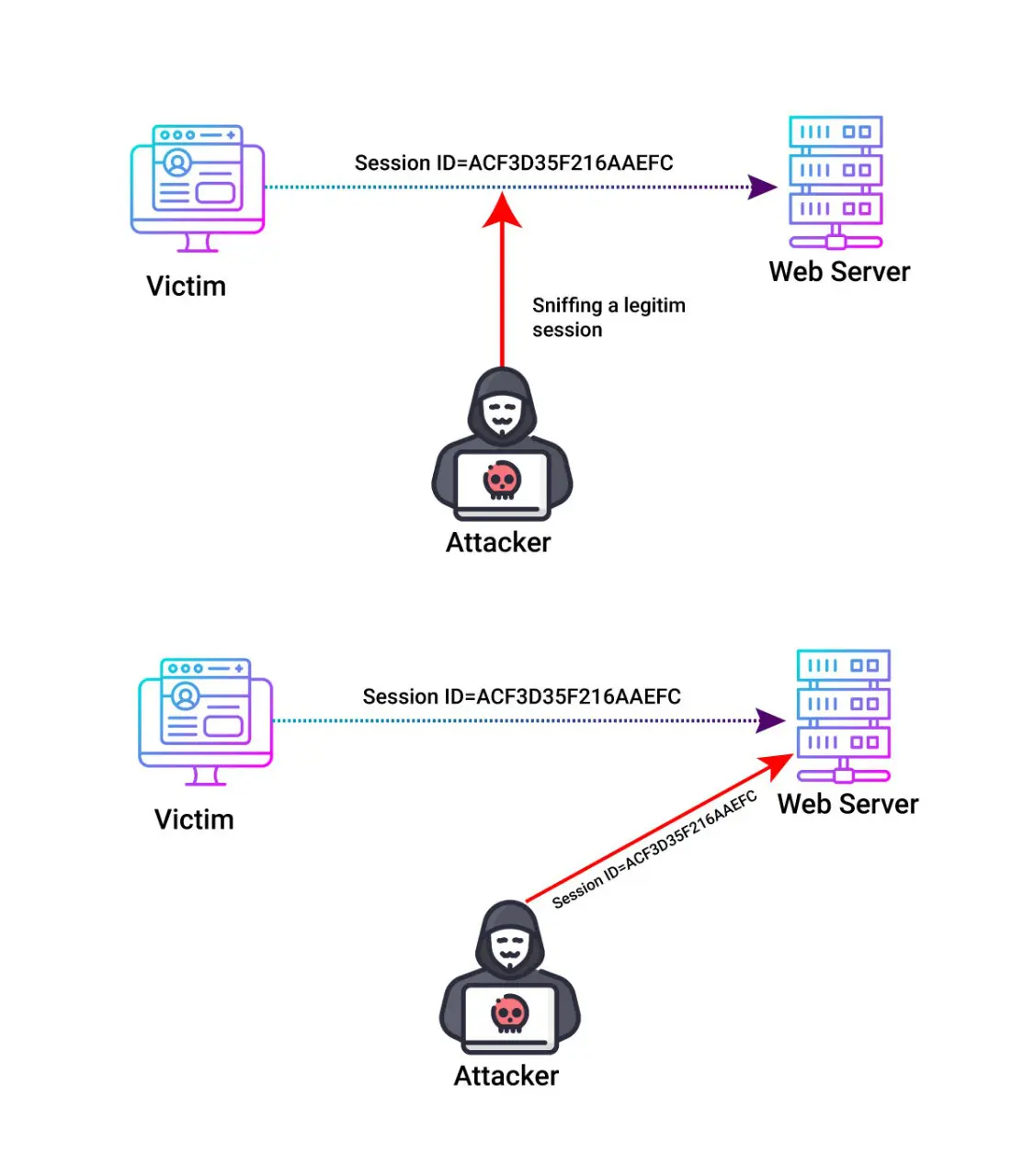
Session Sniffing
In this technique, the attacker uses some packet sniffing tools to obtain the session tokens like session ID of a user and attacker sends requests to the server using this session ID and gains access.
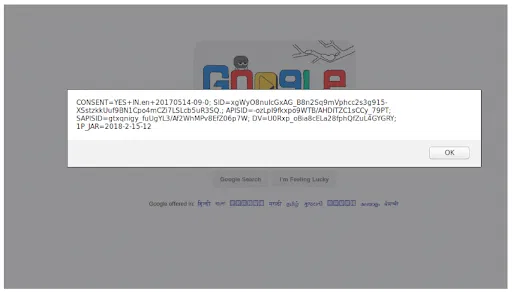
Cross Site Scripting Attack (XSS)
In this technique, the attacker obtains session ID of the user with XSS attack using javascript. For example, if the attacker sends some malicious link to the user and when the user clicks that link, the javascript will execute and the attacker gets the user details.
How to prevent Session Hijacking
-
Use strong passwords
-
Use multi-factor authentication techniques
-
Do not share session IDs with untrusted source
-
Use VPN
-
Always keep softwares up-to-date
-
Avoid using public Wi-Fi












