What Is Remote Code Execution?
Remote Code Execution or RCE, also known as arbitrary code execution is a network vulnerability that allows cybercriminals, from anywhere around the world, the ability to take control remotely of a machine or device, install programs, make changes, create their own accounts, and execute malicious commands, in order to steal sensitive information, destroy data and commandeer network resources for their own purposes like a DDoS attack or other illegal activities.
RCE is comparable to giving a cybercriminal administrative privileges to the systems, machines, and devices. While there are several RCE deliveries or infiltration methods, such as malicious emails and phishing scams, the most common exploit method is through a memory vulnerability in the web browser that occurs when users visit a compromised website. This type of delivery is the hardest compromise to detect. The cyberattackers have to execute arbitrary code on a target to work on this vulnerability. Many uses to introduce the code in the process and by using a vulnerability it changes the program counter to have it point to the code which they use and automatically the injected code gets executed.
How Does it work?
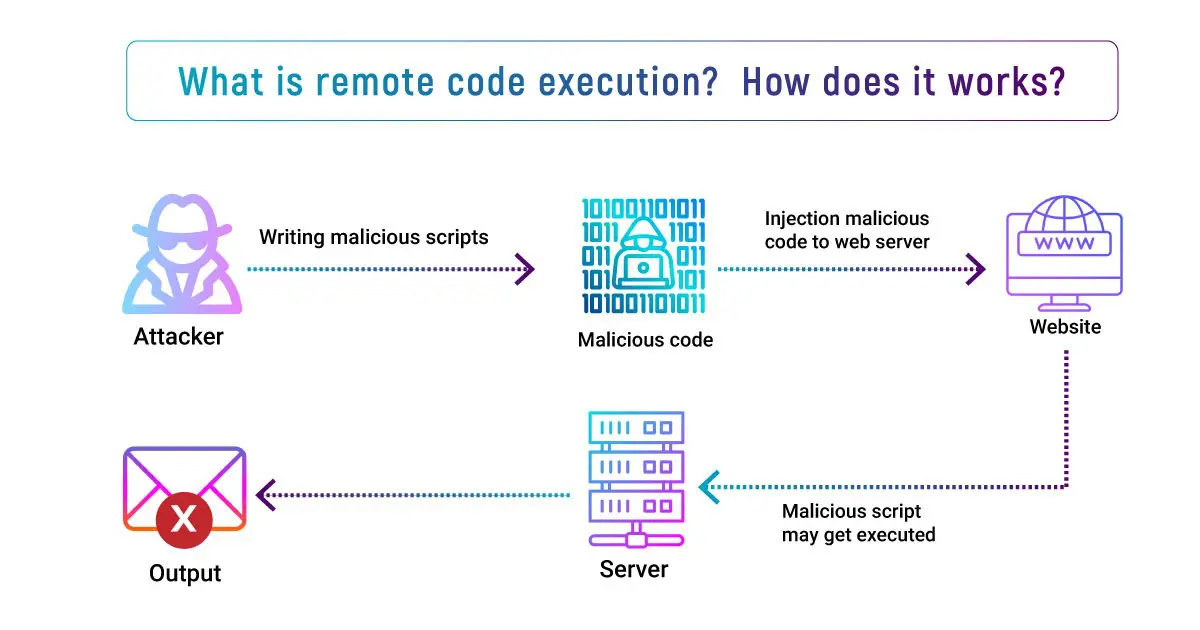
The cybercriminals can achieve RCE in a different ways like:
Injection Attacks :
In many applications like SQL queries, use user-provided data as input to a command. In this attack, the attacker intentionally provides deformed input to be interpreted as a part of command. This enables the cybercriminals to shape the commands executed on the vulnerable system or to execute arbitrary code on it.
Deserialization Attacks :
Most of the Applications use serialization to combine multiple pieces of data into a single string to make it easier to communicate. Specially the user input is formatted with the serialized data which may be interpreted as executable code by the deserialization program.
Out-of-Bounds Write :
Applications frequently allocate fixed size pieces of memory for storing data, including user provided data as well. If this memory allocation is performed incorrectly, an attacker is able to design an input that writes outside of the allocated shield. Since executable code is also stored in memory, user provided data written in the right place may be executed by the applications.
The one common technique that help in controlling of the vulnerable host:
-
Exploit the vulnerability to create a remote shell.
-
Use the default accounts in the selected OS to steal the file password.
-
Use Rainbow tables to break the local Administrator password hash.
-
Use a new administrator password to log in into the system that should be of the same pattern with the same local Administrator password, using Remote Desktop or Server Message Block.
-
If the victim system was acquired by a domain user, for example, a domain administrator for troubleshooting purposes, the victim system may cache that administrator’s password, and that attacker will be able to crack that password in a very short period of time.
-
At last, use the new domain administrator password to log into the system in that domain.
What makes this RCE dangerous is not only the real threats of information theft and also other risks associated with running arbitrary code on the server, but the real difficulty is to detect the defect.This defect may be challenging at best and impossible at its worst. Testing this technique has been around for a while, but effectively defending against it has been a challenge for almost all security vendors. However, as the New York Times aptly observed, they spent billions on US cyber defenses and none of it seemed to work. Few months back in december 21, one RCE vulnerability was found which was named as Log4 Shell found in Log4j, in which there was a JNDI library in which the payload came in and tried to numerate the applications. Many services got affected such as iCloud, Java Edition and Steam and this is marked as the single biggest and most critical vulnerability in the last 10 years.