What is 2FA?
2FA stands for Two Factor Authentication and has become a near requirement for securing user accounts on the internet.
Why do we need 2FA?
The first question that comes to mind when we come to use 2FA as an end user and also as a developer is why do we need it?
To understand that, we need to have a comprehension of how user authentication works. The user is identified by either username, email or both. To authenticate we store the password corresponding to that identifier. That is information that the user knows.
When the username and password information is compromised, the data is accessible to multiple people on the internet. This entails that anyone with the username and password can get access to the account in question.
The idea behind 2FA is to tie the user authentication to, as the name suggests, two factors, i.e., a piece of information that the user knows (password), a piece of information that the user owns or a derivative of the same (software tokens, hardware tokens, biometric information, etc.).
The underlying logic
For this article, I will be talking about 2FA One Time Passwords (OTPs) generated through a software token.
Most of the OTP generation algorithms have two parts to it i.e., a seed (shared secret) and a moving factor.
The seed is shared to the user when the user account is created or when the user opts in to enable 2FA on their account. The moving factor is a variable parameter which is ideally changing every time the user requests a token/ OTP.
HOTP and TOTP are the most popular methods of generating an OTP.
HOTP is the original OTP algorithm and most likely if you opt in to SMS OTP for 2FA, that is the algorithm that is used.
HOTP stands for HMAC based OTP where the initial seed is shared with the user and the moving factor is a counter which denotes the number of times an OTP was requested.
TOTP is the OTP algorithm where the moving factor is based on the current UNIX time. The seed is shared to the user on enabling 2FA and the secret is time based. Unlike HOTP where the tokens do not have an expiry, TOTP tokens generally have a valid period of 30-60 seconds.
The secret can be stored on the client side and UNIX time is used to make a token and this is possible without making any network calls since ideally the client is aware of the current UNIX time. The token is validated on the server-side and the user is logged in.
Authenticator apps like Google Authenticator, Aegis, etc are popular software token based TOTP services.
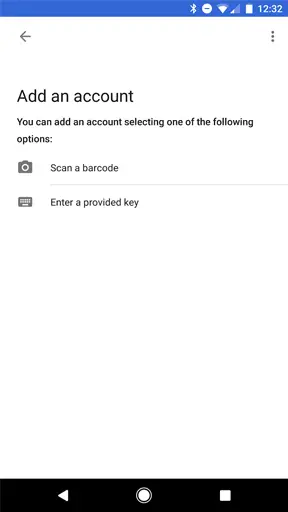
While setting up 2FA, the secret is shared with the client in the form of a QR code or pasted manually.
The QR code is then validated by verifying an OTP to ensure the user has the correct secret.
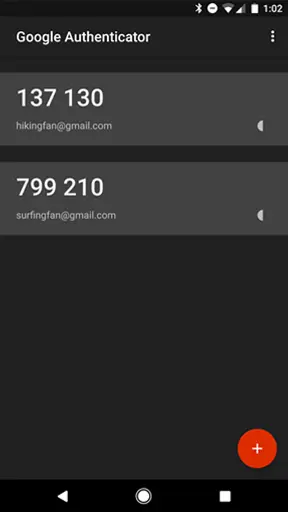
The entry is added on the Authenticator App which keeps on generating OTPs at a 30 sec interval.
Conclusion
While passwords are a secure method of authentication, reused passwords, data breaches threaten the security of just using password based authentication and thus paired with TOTP, it ensures authentication of the user by relying on two factors, password and TOTP.
Even if you are not using an authenticator application for TOTPs, I’d urge you to set up SMS based OTP for 2FA.
If you haven’t enabled 2FA for all your accounts I’d urge you to do the same as soon as you can.












