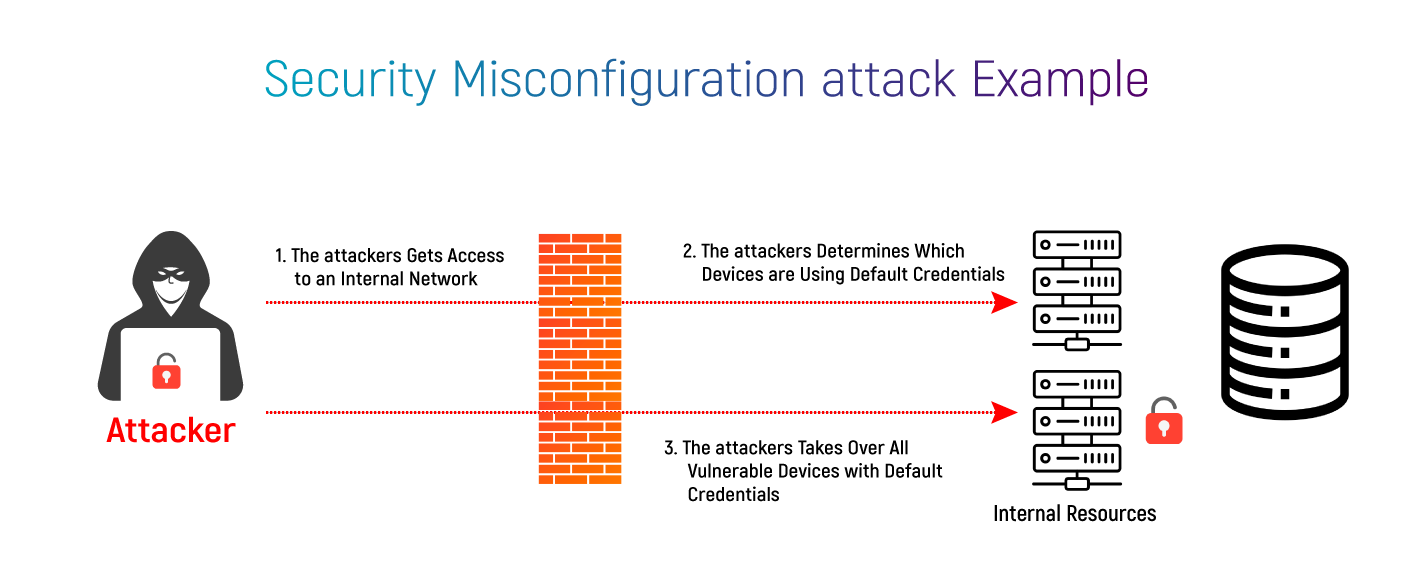
What Is Security Misconfiguration?
What Is Security Misconfiguration? Security misconfiguration refers to the failure to properly configure and maintain the security settings of an application, system, or network. It can occur when default configurations are not changed, unnecessary services are not disabled, or security patches are not applied promptly.
This could have an effect on the network, cloud, or any layer of the application stack. Data breaches costing businesses millions of dollars are frequently caused by misconfigured clouds.
Flexible configuration can be cool however, the more freedom you have to configure your software, the easiest it is to make mistakes.
Common Security Misconfiguration Vulnerabilities:
There are several common security misconfiguration vulnerabilities that attackers often exploit. Some of them are:
Default or weak passwords:
Attackers can easily guess or crack default or weak passwords to gain unauthorized access.
Outdated software:
Outdated software often contains known security vulnerabilities that can be exploited by attackers.
Unsecured network ports:
Unused or unsecured network ports can be exploited to gain unauthorized access or perform attacks such as port scanning.
Insecure protocols and configurations:
Insecure protocols and configurations can lead to data leakage, man-in-the-middle attacks, and other security issues.
Improperly configured web servers:
Misconfigured web servers can expose sensitive data or allow attackers to execute arbitrary code.
Lack of proper access controls:
Lack of proper access controls can allow attackers to bypass authentication and gain unauthorized access to sensitive data or systems.
Poor logging and monitoring:
Poor logging and monitoring can make it difficult to detect and respond to security incidents.
Impact of Security Misconfigurations Attacks:
Security misconfiguration attacks can have a significant impact on cybersecurity. These types of attacks occur when systems, applications, or network devices are not configured correctly, leaving vulnerabilities that can be exploited by attackers. The impact of security misconfigurations attacks includes,
Data breaches:
Attackers can gain access to sensitive data, such as customer information, financial records, or trade secrets, through security misconfiguration attacks. This can result in the loss of confidential data and damage to a company’s reputation.
Malware infections:
Misconfigurations can make systems vulnerable to malware infections, where attackers can gain control of systems, steal data, or use them for malicious purposes. Malware infections can also lead to system downtime, data loss, and operational disruptions.
Denial of service attacks:
Misconfigurations can leave systems vulnerable to denial-of-service attacks, where attackers flood systems with traffic or requests, causing them to crash or become unavailable. This can result in significant operational disruptions, loss of revenue, and reputational damage.
Compliance violations:
Misconfigurations can lead to compliance violations with industry regulations and standards, such as the Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA), and General Data Protection Regulation (GDPR). These violations can result in fines, penalties, and legal consequences.
Reputation damage:
Security misconfigurations can damage an organization’s reputation and erode customer trust. This can result in loss of business, revenue, and market share.
Overall, security misconfiguration attacks can have serious consequences for an organization’s cybersecurity, financial stability, and reputation. It is crucial to prevent and address misconfigurations promptly to mitigate their impact.
How Can You Prevent Misconfiguration Issues?
Misconfiguration issues are one of the most common causes of security breaches. To prevent misconfiguration issues in cybersecurity, here are some best practices to follow:
Implement security configuration standards:
Establish and enforce security configuration standards for all systems and devices used in your organization. These standards should be based on industry best practices and regulatory requirements.
Regularly update and patch systems:
Make sure that all systems and applications are up-to-date with the latest security patches and updates. Regularly check for vulnerabilities in your systems and promptly patch any vulnerabilities that are found.
Use strong passwords:
Use strong passwords for all systems and devices. Passwords should be at least 12 characters long and should include a mix of upper- and lower-case letters, numbers, and special characters.
Implement two-factor authentication:
Implement two-factor authentication for all systems and devices. This will add an extra layer of security and make it more difficult for attackers to gain access to your systems.
Restrict access:
Limit access to systems and devices to only those who need it. Use role-based access controls to ensure that users have access only to the resources that they need to perform their job duties.
Regularly monitor logs:
Regularly monitor system logs for any unusual activity. This can help you detect potential security threats before they become a problem.
Perform regular security assessments:
Perform regular security assessments to identify potential misconfiguration issues and vulnerabilities in your systems and devices. Address any issues that are identified promptly.
Provide regular security training:
Provide regular security training to employees to educate them on the importance of security and how to recognize and report potential security threats.
To achieve this, you must have a real-time and accurate map of your whole infrastructure. This demonstrates communication and flows over your data centre environment, both on-premises or in a hybrid cloud.