
Why Is Virtual Patching So Important?
Virtual Patching gives a rapid way of a solution to provide web security. Even though the preferred solution is temporary, it
Website Security using Web Application Firewall – Prophaze WAF

Virtual Patching gives a rapid way of a solution to provide web security. Even though the preferred solution is temporary, it

From the technical point of view, the initial mitigation strategy would be for an organization to rectify the discovered vulnerability

Key Terms : Nodes: Virtual host(s) on which containers/pods are running. Kubernetes Service: A logical set of pods that perform

Key Terms: Pods: One or more containers that shares the storage and network with a Kubernetes configuration, mentioning the behavior
Kubernetes Security: Build Phase Securing containers and Kubernetes starts within the building part with securing your container images. Your time
Overview : Around 87% of organizations are using Kubernetes container orchestration to manage their container workloads. Each of the security
Cyber landscape predictions FireEye Mandiant has delivered its cyber landscape predictions for the coming year, including growing and affiliate-supported espionage,
Overview : Multiple vulnerabilities reported in GitLab EE. Affected Product(s) : Affected versions are >=10.2, =13.4, =13.5, =8.12, =13.4, =13.5,
Overview : Cross-Site Scripting (XSS) vulnerability on API Manager 3.1.0. Affected Product(s) : WSO2 API Manager Vulnerability Details : CVE
Prototype Pollution Prototype Pollution is a vulnerability affecting JavaScript. Prototype Pollution refers to the ability to inject properties into existing
CVE-2019-20901 Proof of Concept : The login.jsp resource in Jira before version 8.5.2, and from version 8.6.0 before version
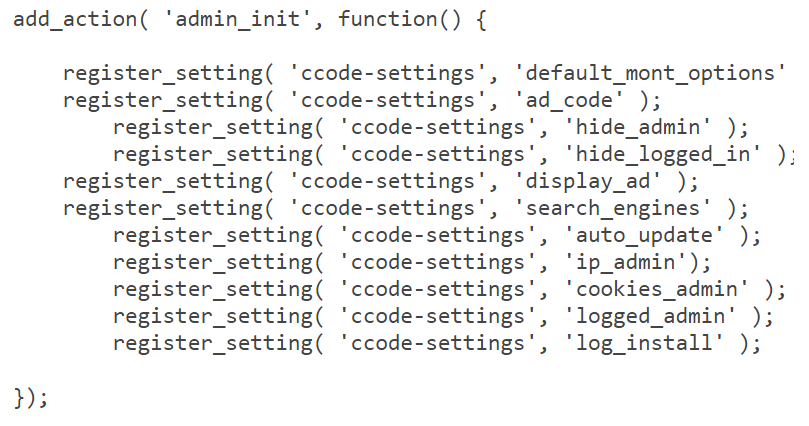
A new variant of popup injector WordPress malware is spreading and affecting 1000s of WordPress websites. The web master was
Overview : In phpMyAdmin 4.x before 4.9.5 and 5.x before 5.0.2, a SQL injection vulnerability was found in retrieval of
Overview : cs/service/account/AutoCompleteGal.java in Zimbra zm-mailbox before 8.8.15.p8 allows authenticated users to request any GAL account. This differs from the
Overview : Dell EMC Data Protection Advisor versions 6.3, 6.4, 6.5, 18.2 versions prior to patch 83, and 19.1 versions
Overview : LogicalDoc before 8.3.3 allows SQL Injection. LogicalDoc populates the list of available documents by querying the database. This
Overview : Trend Micro Worry-Free Business Security (9.0, 9.5, 10.0) is affected by a directory traversal vulnerability that could allow
Overview : SuiteCRM 7.10.x versions prior to 7.10.23 and 7.11.x versions prior to 7.11.11 allow for an invalid Bean ID
Overview : cPanel before 84.0.20 allows a demo account to achieve remote code execution via a cpsrvd rsync shell (SEC-544).
Overview : OpenCart 3.0.3.2 allows remote authenticated users to conduct XSS attacks via a crafted filename in the users’ image
Overview : Umbraco CMS 8.5.3 allows an authenticated file upload (and consequently Remote Code Execution) via the Install Package functionality.
Overview : Citrix SD-WAN 10.2.x before 10.2.6 and 11.0.x before 11.0.3 has Missing SSL Certificate Validation.An information disclosure vulnerability has
Overview : cPanel before 82.0.18 allows attackers to leverage virtual mail accounts in order to bypass account suspensions (SEC-508). Affected
Overview : SuiteCRM 7.10.x versions prior to 7.10.23 and 7.11.x versions prior to 7.11.11 allow for an invalid Bean ID