
Web Application Firewall for Startups
A web application firewall for startups is vital to keeping data safe. Even the smallest teams can be vulnerable to

A web application firewall for startups is vital to keeping data safe. Even the smallest teams can be vulnerable to

Web applications form a massive part of the common network ground that is shared by a business and its customers

Software vendors have identified many areas in which they could improve their offerings in order to better serve their customers

Cyber attacks are one of the fastest-growing crimes in the cyber world. Cyberspace has become a major force in today’s
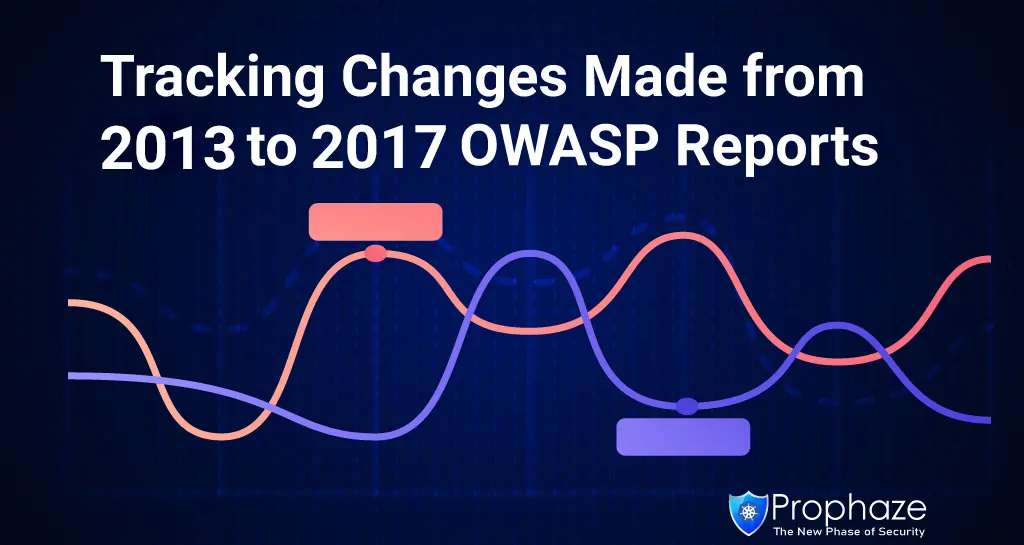
OWASP Top 10: 2017 Edition in Comparison with 2013 Edition Image Source: https://owasp.org/www-pdf-archive/OWASP_Top_10-2017_%28en%29.pdf.pdf Major Changes Introduced from 2013 to 2017 Change

Website security refers to the security of organizational and private public-facing websites from various cyber-attacks. These attacks largely impact all

A website being hacked here and there isn’t exactly news to everyone around us, but for a business owner whose

Everyone knowing about OWASP must be curious about what’s modified withinside the Top 10 for 2021. Here’s What’s New in
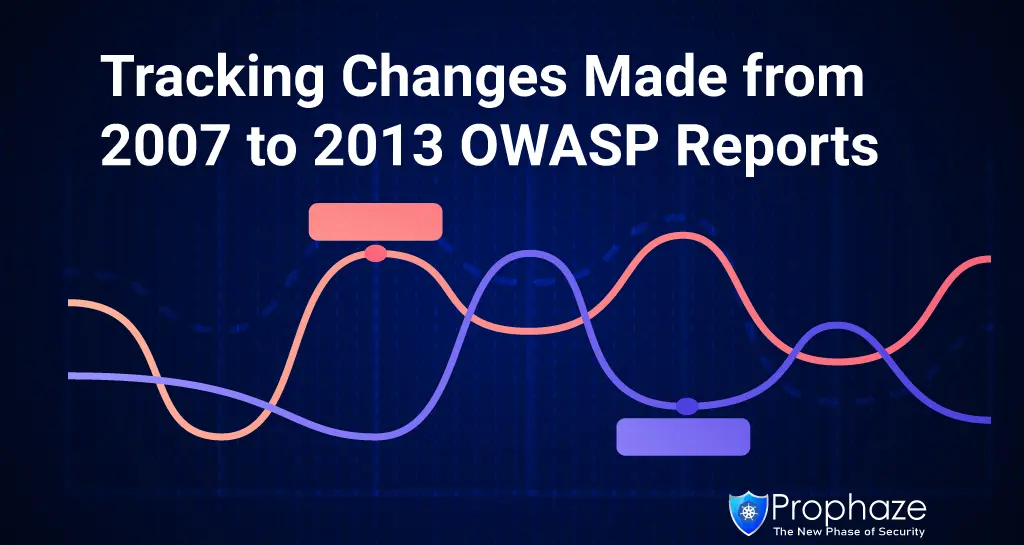
Tracking Changes Made from 2007 to 2013 Reports OWASP analyses the most crucial web application security flaws. OWASP being a

What is OWASP & How It Functions? The Open Web Application Security Project (OWASP), founded in 2001 with the intention

A cloud WAF is also known as a cloud-based WAF or cloud-native WAF and it provides web application security more

Application security is the method that is used to secure web apps. In this we find, fix and enhance the

A web application firewall (WAF) secures a web application such as websites from several application attacks such as cross-site scripting

Software-as-a-service (SaaS) security is usually considered as the basic process of users surfing the web. Digging a little deeper reveals

Cloud is a transformative piece of technology that can put an immediate solution when a business opportunity is present. Cloud

Cyber breaches have always been a concern for businesses across all industries. Their after-effects lead to compromised customer loyalty &

Cloud computing mainly aims at providing fast, easy-to-use computing and data storage services at a low cost. Cloud environment does

Since COVID-19 has hit the world with its wrath, the business world has turned upside down, companies are shifting to cloud-native

A vulnerability was found in Gradle up to 7.1 on Unix. It has been declared as critical. Affected by this

A lot of people aren’t aware of the nature of the term “serverless” and to understand the gravity of the

The universe is full of secrets and almost everything surrounding you has tons of secrets just waiting to be discovered.

The cloud market has seen an exponential increase in 2020 and this trend was observed amid the steepest economic contraction

Cloud computing has become the new norm, especially during & post- pandemic world. With businesses moving online, cloud security is

The core to any container security effort is testing the code and supplementary components which will execute within containers, and