The term patch is misleading because the vulnerable system is not being patched. A quick repair job for a piece of software code is called a patch. It is developed and distributed as a replacement or insertion of rule(s) to restrict the inputs and outputs to the vulnerable application in an intermediary layer.
Virtual Patching is not a web application specific term but can be applied to other protocols also. Currently, it is more generally used as a term for Web Application Firewalls (WAF). An application firewall is an enhanced firewall that limits access to a computer’s operating system by specific application programs.
Definition: Virtual Patching
Open Web Application Security Project (OWASP) defined Virtual patching as:
“Security policy enforcement layer which prevents the exploitation of a known vulnerability.”
The virtual patch works once the security enforcement layer analyses transactions and intercepts attacks in transit, therefore the malicious traffic never gets to the web application. The impact of virtual patching is that without updating the source code, it prevents an exploit from occurring.
It is the quick development and short-term implementation of a security policy. As a result, the organization would get more time to spend to evaluate the risks associated with the vulnerability in their environment and develop a mitigation strategy.
A code patch provided by a vendor, deep security virtual patching protects against particular exploits. The patching is deployed at the network level. Virtual patching is also called proximity control because it can block a threat before it exploits its target. It can be considered as an emergency security tool that organizations will use to address vulnerabilities on affected endpoints and servers instantly.
In certain situations, the organization can address the vulnerability at the application level also. This allows virtual patching rules for that vulnerability to be removed. In other situations, the rules specific to that vulnerability may remain in effect where actual patching is not feasible or cost-effective.
It is very important to follow the same kind of IT controls that are needed for any other system in the company’s environment, for the effective management of testing, deployment, and retirement of the rules. The controls include code management, SDLC controls, Technology Asset Management, Change Management, and Configuration Management.
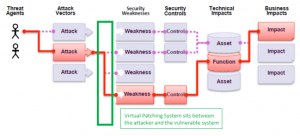
Considering everything about the software on the network including the versions and patch levels will help analysts to decide where the virtual patching devices need to be placed. The organization must have an up to date network map that details the different inbound and outbound paths to the applications. Else, a path could be left unprotected, or a device could be deployed in a network path that is not at risk. The below figure shows the virtual patching device must sit between the attacker and the system that has the vulnerability.
See the below links:
(a) Introduction to Virtual Patching