“Virtual Patching” is a term that was initially used by Intrusion Prevention System vendors many years ago. It is also known as External Patching or Just-in-time Patching. This term is not only web-application specific but mainly used by WAF providers over the past years.
In today’s dynamically changing IT world, new vulnerabilities are known at an increasing pace and attackers to have become more sophisticated in their ability to take advantage of these vulnerabilities. Most of the successful cyber-attacks can involve vulnerabilities identified to company executives. The high severity vulnerabilities, that aren’t patched for the future are extremely liable to error and it is not possible to defend from attackers. The most acceptable solution is fixing that type of code editing to rectify code flaws in applications and OS.
Patching systems to reduce security vulnerabilities could be a regular open-ended activity, fraught with the dual risk of putting in either a bad patch or the system turning into compromised because of a patch that has not been installed. The decision of patching or not is ruled by the trade-off between the danger of wrong patch installation, versus the danger of penetration, which pits two equally vital problems against one another. Patching an important system could break it and failing to do so could leave it open to a security vulnerability.
Failure to patch vulnerabilities in code will cause data loss which will value over what your company can afford to pay. An example of software system fixing failure came from a small non-profit company. For example, a company needs to pay federal regulators an amount as fines for permitting their system to be breached by not fixing their software package. That penalty is on high of the prices that they’re going to incur in fixing the systems they didn’t patch within the initial place.
There are several different advantages to applying software patches, together with adding options and fixing bugs that build the code run slow or not work right. All software package has to be patched. Whether or not the software package sits on a disk and runs on a server, resides on a chip at intervals a firewall, or is an app that’s in your tablet devices, it all has to periodically be updated and patched to be secure.
With Virtual patching, you’ll avoid this drawback entirely and you’ll get it on quickly, cheaply, safely, and while not having to patch any system or being forced to decide on between choices. Virtual patching, permits you to patch your web application, while not touching the application, its libraries, OS, or maybe the system it is running on. In technical terms, Virtual patching may be a technique of fixing a retardant by fixing or eliminating a vulnerability by dominant either the inputs to its application through an external application, shim, proxy, or virtual server. The safer possibility is to use the previous, as against the latter. The latter methodology is even as viable, but in this case, you’re ever-changing the application itself, which might present alternative risks. The safest, and equally impact technique, is to encapsulate the application and to manage the inputs into or outputs from the application to stop or eliminate aberrant behavior. You primarily offload the whole issue to one thing external to your system and with fewer moving components, thus reducing your operational and security risk.
Nowadays, heavy usages of third-party components in web development practices become more popular. The plugin developer required to push an update in fixing the vulnerable code within the third-party components usually.
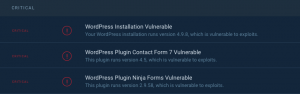
We have seen reported vulnerabilities keep without a fix for several weeks or even months. For website owners/developers, analyzing the code and manually fixing is typically not a choice.
That’s where virtual patching come very handy.
See the link : https://prophaze.com/virtual_patching/









