Safeguarding the company’s assets against existing and emerging vulnerabilities is the most critical task that security teams are struggling with. Virtual Patching can be a great choice for corporate having multiple websites. The central management of virtual patching can save a lot of time, if the sites have the same framework/CMS/plugins are installed.
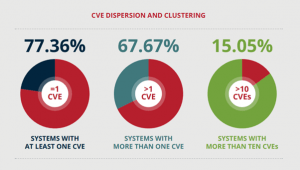
According to the Vulnerability Statistics Report (2020) by Edgescan, on average of 67.7% of organizations’ assets have at least one CVE (Common Vulnerabilities and Exposures). Here is CVE dispersing and clustering:
To prevent possible misuse, the most simple method is to patch the system against flaws with a software patch developed. Identifying vulnerabilities and addressing them with patching is a must for both externally and internally facing systems. It might be an exploit point for offenders, even though the vulnerability is not a critical one. Continuous vulnerability identification and control over inbound and outbound traffic are important to enhance malware resilience.
Few reasons why virtual patching is great for web sites:
- It’s scalable as managed web application firewalls can deploy patches to a network of sites at the same time.
- It reduces the risk while the developer of a plugin/component releases the fix.
- Less risk for conflicts compared to when the code is manually patched.
- It provides protection to all sites almost immediately after discovery.
- Reduces time and money from remediation or from manual code patches.
How to apply Virtual Patch on your website?
Virtual patches are often created by a dedicated security team. They are not creating rules on how the traffic flows on all the sites when specific conditions are met.
- Endpoint Web Application Firewalls:
It can’t be bypassed and is often more aware of the environment of the website. Because it is installed inside the web application.
- DNS Firewalls:
It is installed in front of the website’s traffic, therefore the whole traffic to the website is routed through a third-party server. The firewall engine in the server analyses traffic and does its filtering. It is not aware of the application internals and it can be completely bypassed, only if the original website IP is known.
If there is an issue, where patching might affect the application’s core functionalities, it may take weeks or months to patch a vulnerable.
Some challenges make patching even longer:
- Cost Reduction
- Official Patch Deployment
- Uptime Preservation
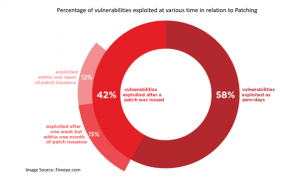
FireEye Mandiant Threat Intelligence Research suggests that the majority of the vulnerability exploitation happens either before the issuance of the patch or within few days of the patch was issued.
The necessity of patching is directly proportional to the speed with which hackers exploit. The patching delay means the enterprise is at risk of attacks, and the offenders might collect all the details they need to exploit, which involve the following issues:
- Security measure compromise
- Critical Data Exposure
- Network and System Compromise
- Reputational Loss
- Financial Loss
Technologies like deep security virtual patching can aid this patching management process by shielding both known as well as unknown vulnerabilities.
See the below links: