
Preparation Phase, Identification Phase and Analyze Phase
Preparation Phase The significance of adequately utilizing the preparation phase in respect of virtual patching can’t be overstated. Before dealing with a discovered vulnerability,

Preparation Phase The significance of adequately utilizing the preparation phase in respect of virtual patching can’t be overstated. Before dealing with a discovered vulnerability,

Patch Management is a strategic process of acquiring, testing, and installing updated software. But, most of the companies find themselves

“Virtual Patching” is a term that was initially used by Intrusion Prevention System vendors many years ago. It is also
Why would your Business need VAPT? It is very necessary to conduct a network security audit periodically to ensure the
WAF for Kubernetes Unleash Your Online Potential with Our Innovative Web Solutions Prophaze meets the challenge head-on to successfully defend
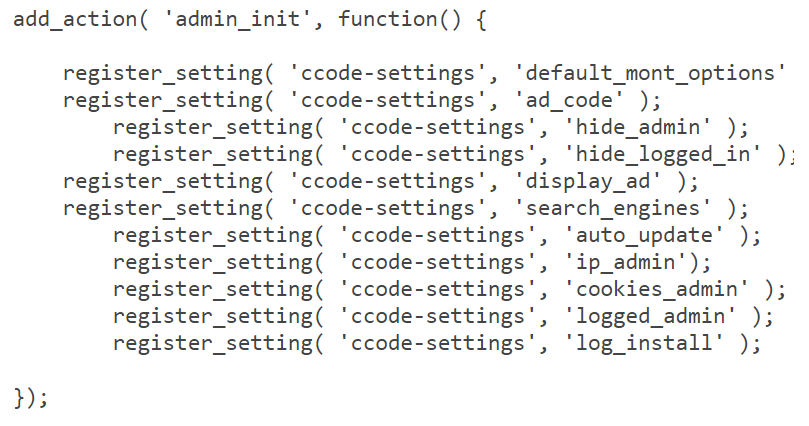
A new variant of popup injector WordPress malware is spreading and affecting 1000s of WordPress websites. The web master was
TERMS OF SERVICE (SAAS) PROPHAZE INDIA PVT. LTD. AND/OR ITS AFFILIATES (“PROPHAZE”) IS WILLING TO GRANT ACCESS TO THE SAAS
Integrations Streamline Your Security Infrastructure with Prophaze Integration Prophaze web application firewall is designed to protect web applications from a
Virtual Patching Prophaze WAF’s Mitigating Vulnerabilities in Web Applications Prophaze WAF’s virtual patching features in mitigating vulnerabilities of web applications.
Compliance Ensuring Regulatory Compliances and Best Practices E-commerce, FinTech, Health Tech, and organizations that process PII and PHI data find
Why Prophaze? Prophaze’s solutions are designed to protect their web applications and APIs against a variety of risks, including both
Overview : Fuji Electric V-Server Lite all versions prior to 4.0.9.0 contains a heap based buffer overflow. The buffer allocated
Overview : In Rockwell Automation RSLinx Classic versions 4.1.00 and prior, an authenticated local attacker could modify a registry key,
Overview : In Argo versions prior to v1.5.0-rc1, it was possible for authenticated Argo users to submit API calls to
Overview : Privilege escalation vulnerability in MicroK8s allows a low privilege user with local access to obtain root access to
Overview : On BIG-IP 15.1.0-15.1.0.1, 15.0.0-15.0.1.1, and 14.1.0-14.1.2.2, under certain conditions, TMM may crash or stop processing new traffic with
Overview : LogicalDoc before 8.3.3 allows SQL Injection. LogicalDoc populates the list of available documents by querying the database. This
[vc_row][vc_column width=”1/2″][vc_empty_space height=”15px”][vc_column_text][/vc_column_text][/vc_column][vc_column width=”1/2″][vc_empty_space height=”15px”][vc_column_text] Bot Detection The Problems 20% of all web traffic is bad bots targeting APIs to
[vc_row][vc_column width=”1/2″][vc_empty_space height=”15px”][vc_column_text][/vc_column_text][/vc_column][vc_column width=”1/2″][vc_empty_space height=”15px”][vc_column_text] WAF for your API Gateway Prophaze EagleEye can secure your API end points against OWASP

Overview : PrivateBin versions 1.2.0 before 1.2.2, and 1.3.0 before 1.3.2 has an Arbitrary File Upload Vulnerability Affected Product(s) :

Overview : Prizm Content Connect 5.1 has an Arbitrary File Upload Vulnerability Affected Product(s) : Prizm Content Connect 5.1 Vulnerability

Overview : SO Planning is an open source online planning tool completely free, designed to easily plan projects / tasks

Overview : RSA Authentication Manager versions prior to 8.4 P7 contain an XML Entity Injection Vulnerability. A remote authenticated malicious