Web Attacks Are Evolving Fast Prophaze AI WAF Stops Them at the First Request
Full‑lifecycle, AI‑driven WAF protection for cloud, Kubernetes, hybrid, and on‑prem applications—predict, detect, and block zero‑day attacks, bots, and Layer 7 DDoS with adaptive machine learning that safeguards every request without impacting performance or DevOps velocity.
- Kubernetes-Native WAF
- OWASP Top 10 Protection
- Bot & DDoS Defense
- Zero code setup
- Any-Cloud Ready
- Layer 7 Zero-Day Block
Web Attack Surface Is Expanding
Faster Than Security
Web applications are no longer static websites. They are API-driven, cloud-connected, constantly changing systems 24/7. Before you can defend web applications, you need visibility into how they’re being targeted. Static, rule-based WAFs struggle with evolving attack techniques, encrypted traffic, and automated abuse. Prophaze WAF continuously analyzes live traffic patterns to detect and stop threats that bypass legacy controls.
Signature-based WAFs failing against zero-day exploits

High false positives disrupting real users

Bots imitate real users and evade static rules

Fragmented protection across cloud, Kubernetes, and on-prem
A Unified WAF Platform Designed for
Modern Web Architectures

AI-powered threat detection that adapts in real time

Zero-day attack prevention before signatures exist
Bot mitigation for scraping, credential stuffing, and abuse

Layer 7 DDoS protection using behavioral rate controls

Fine-grained policy enforcement per application

Compliance-ready security aligned with OWASP, PCI-DSS, and HIPAA
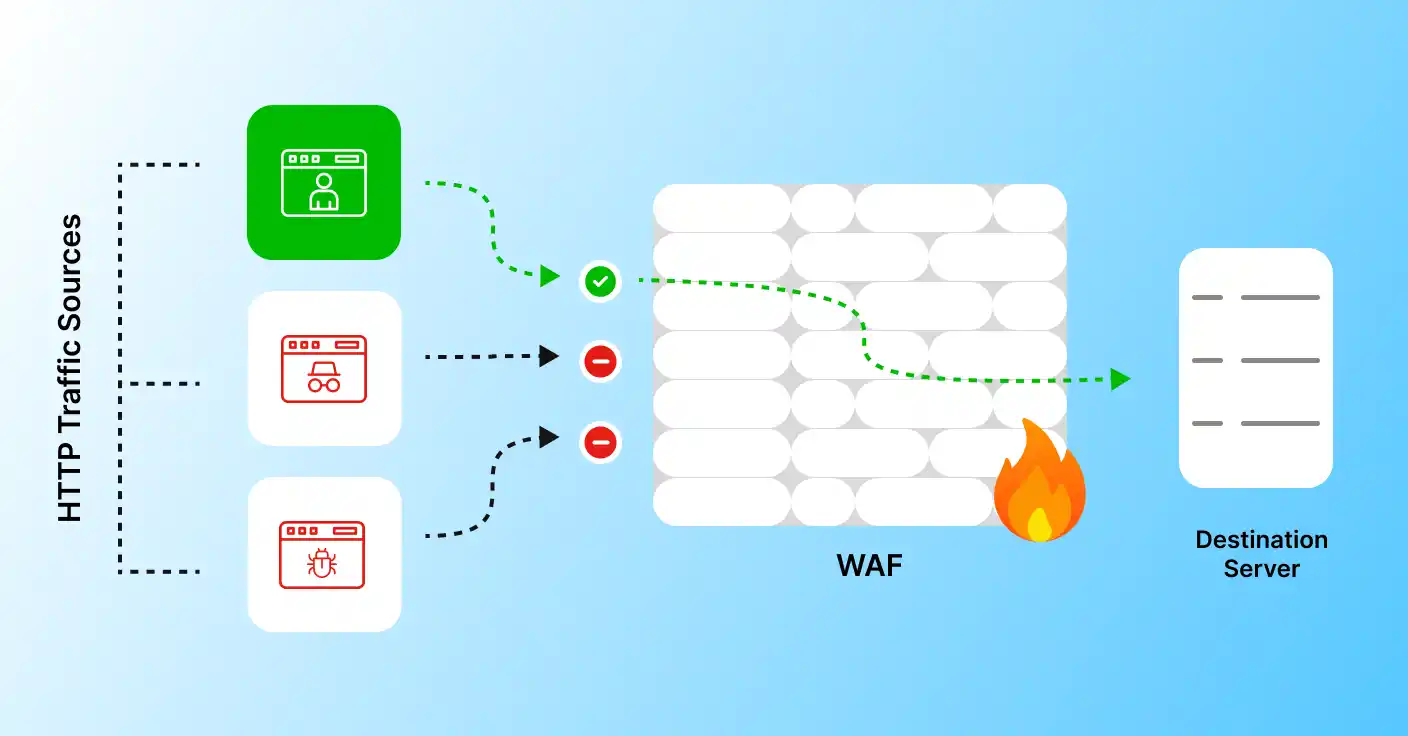
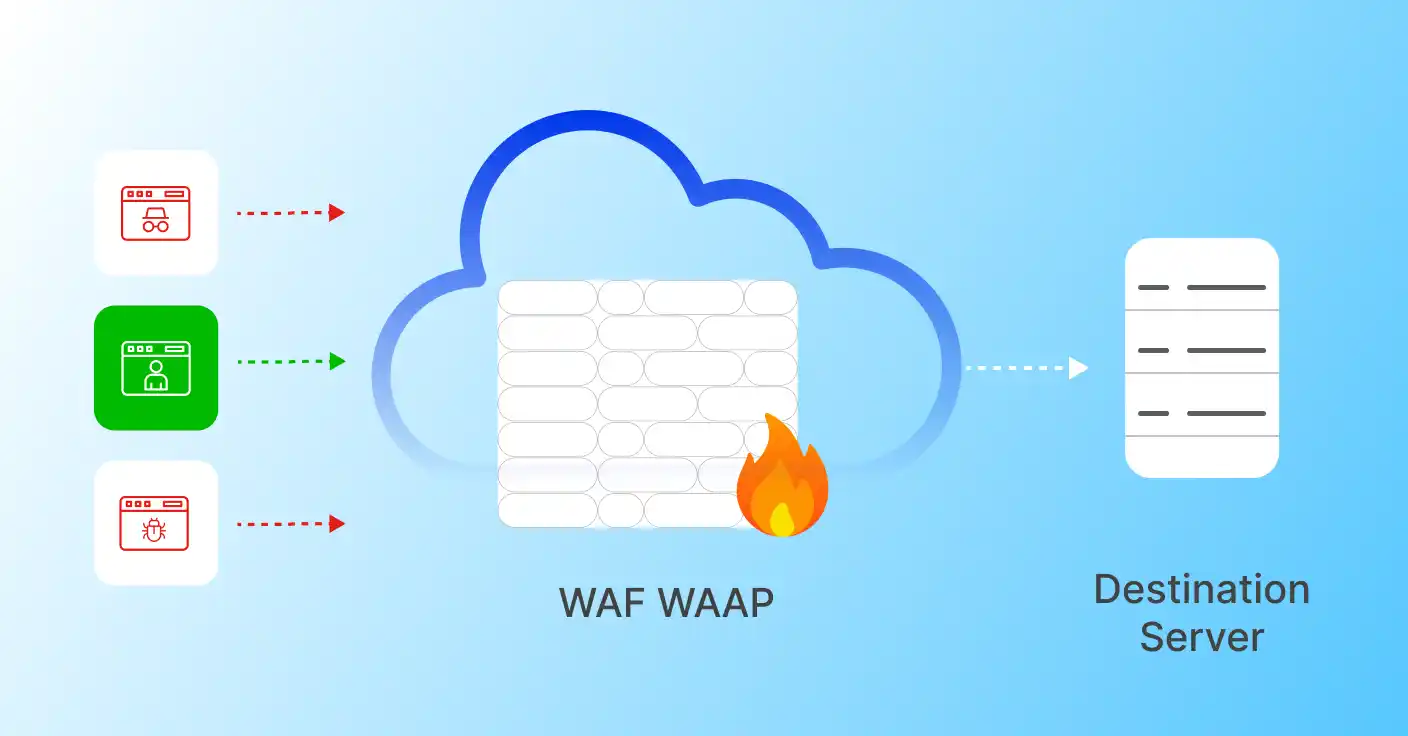
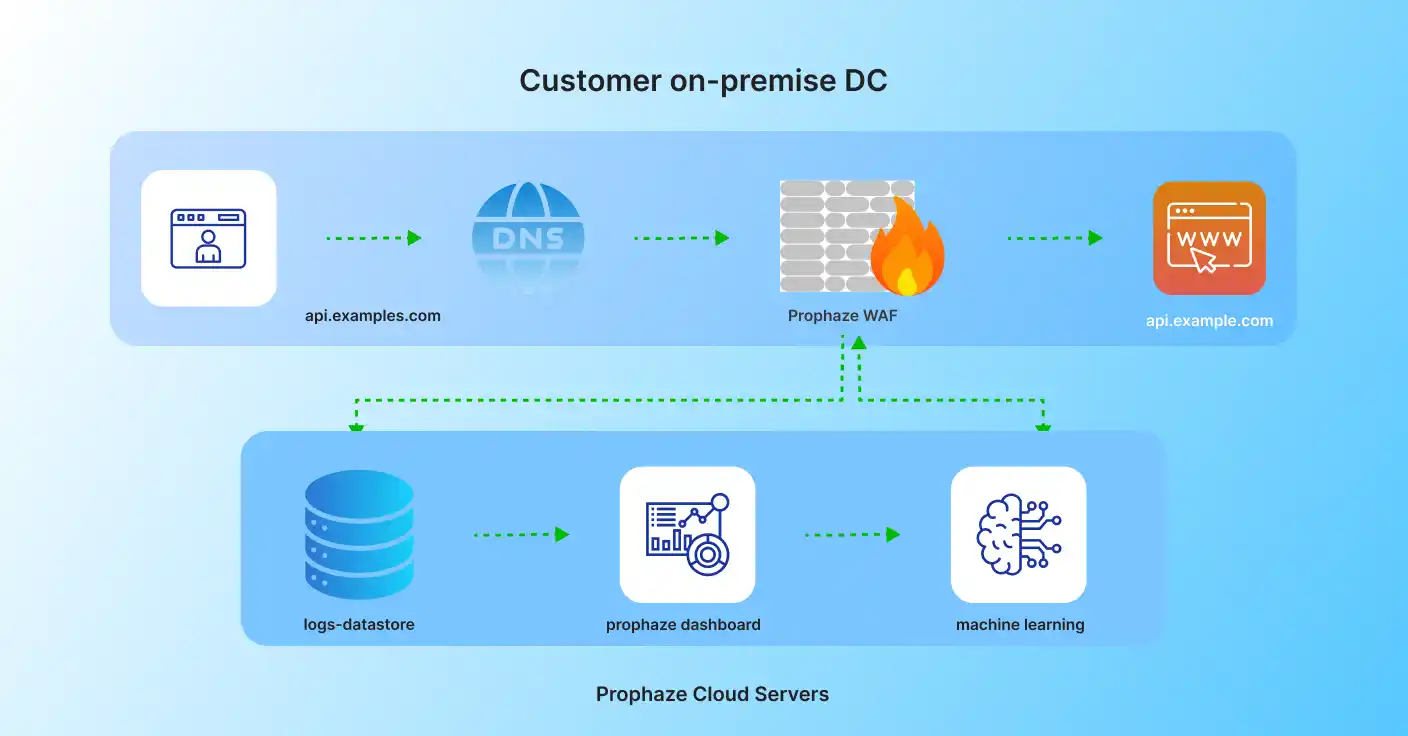
How Prophaze WAF Engine Protects APP in Real-Time
Prophaze WAF inspects traffic inline or at the edge using AI-driven analytics to distinguish legitimate users from attackers—without interrupting normal application behavior.
Traffic Ingestion
Captures HTTP/HTTPS traffic with no code changes
Behavioral Analysis
Builds baselines for normal user and bot behavior
Real-Time Mitigation
Blocks, challenges, or rate-limits malicious traffic

Prophaze
Hybrid WAF
Deep Inspection
Analyzes headers, parameters, cookies, and payloads
Anomaly Detection
Flags unusual request patterns and payload structures
Continuous Learning
Models evolve as traffic and attack methods change
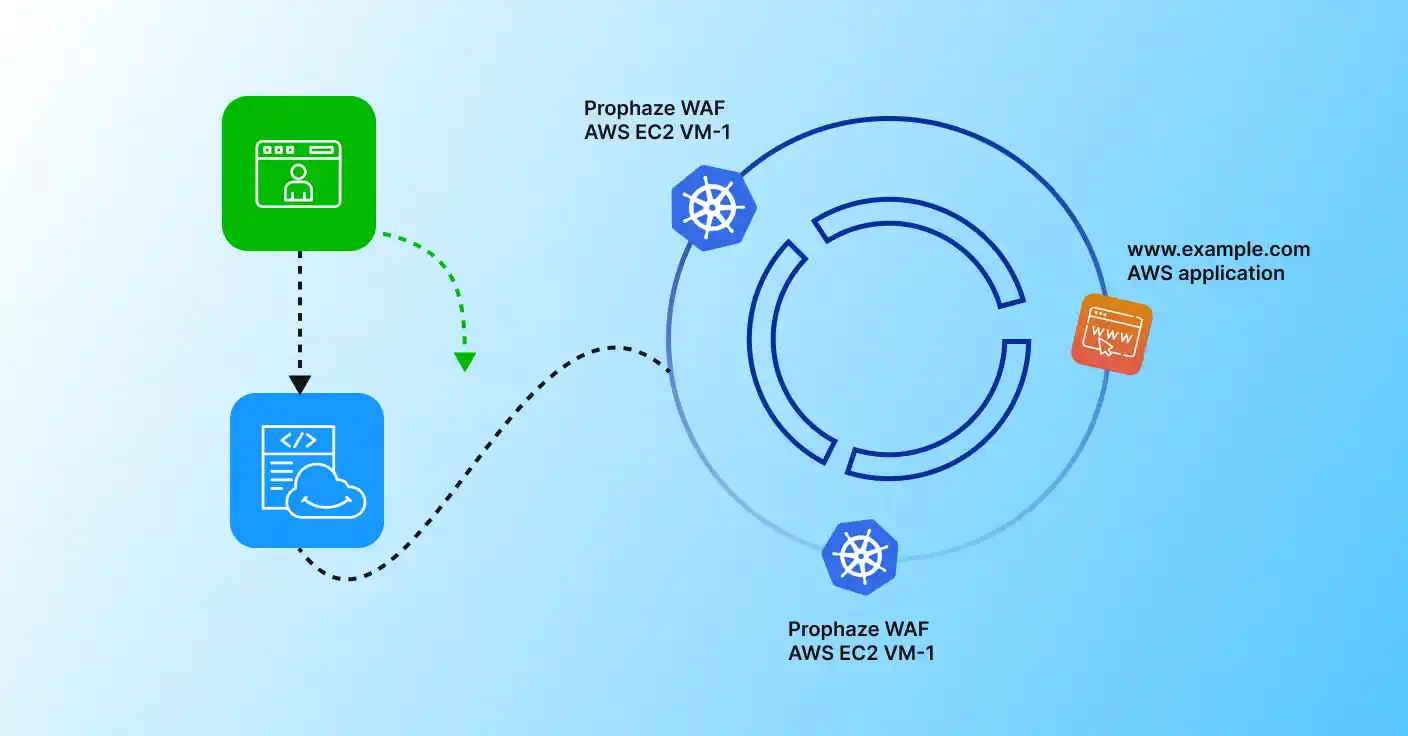
Flexible Deployment Models Powered by a Single WAF Engine
Prophaze WAF adapts to your infrastructure—not the other way around—ensuring consistent security across all environments.
From First Request to Full Control —in Three Moves
Observe and understand application behavior
- Automatically analyze live HTTP and API traffic to learn how users, bots, and services normally interact with each application.
- Establish dynamic baselines for endpoints, parameters, methods, and session flows—without manual tuning or predefined assumptions.
Identify threats with context
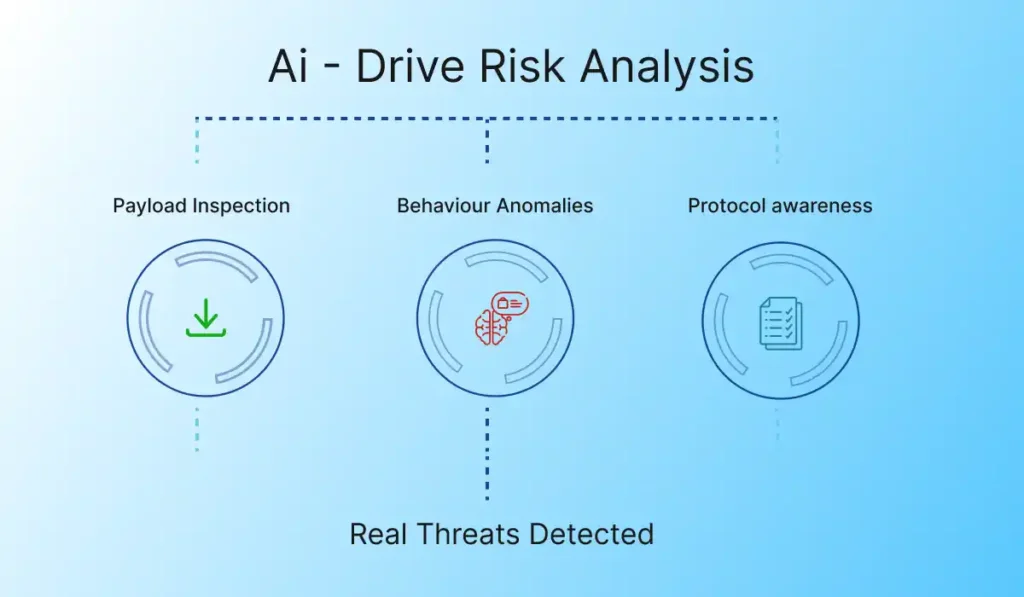
- Evaluate every request using AI-driven risk analysis that combines payload inspection, behavior anomalies, and protocol awareness.
- Surface real threats such as exploits, automation, abuse, and Layer-7 floods—while reducing false positives that disrupt users.
Enforce consistent policies everywhere
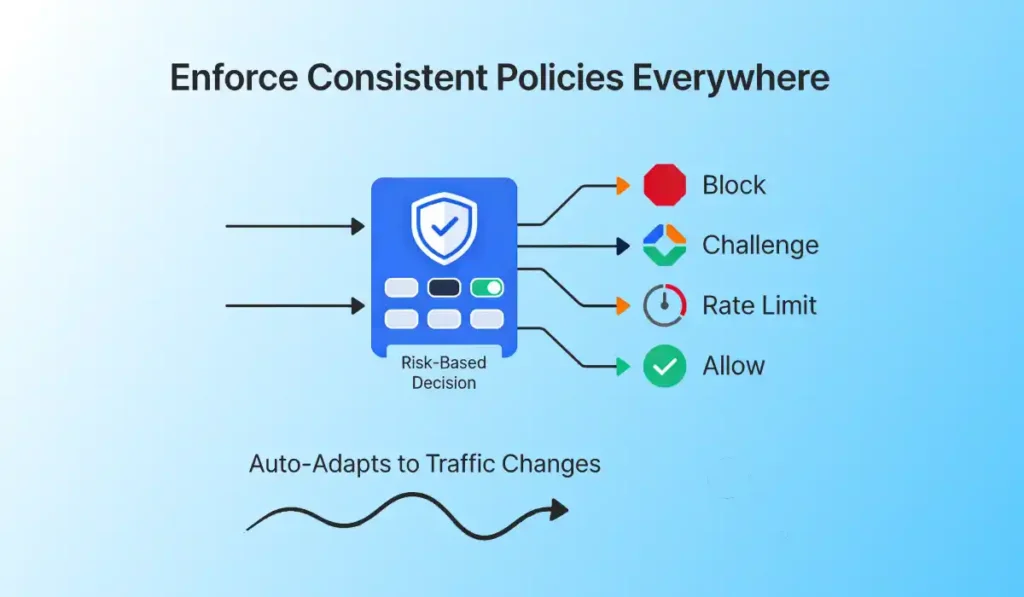
- Apply the right response in real time—block, challenge, rate-limit, or allow—based on risk and business impact.
- Policies adapt automatically as traffic patterns change, ensuring protection stays effective without constant rule maintenance.
- Healthcare
- API Security
- Bot Mitigation
Healthcare Deflecting 250 Million Application & API Attacks on Healthcare Systems with Prophaze WAAP
DevSecOps Fighting False Positives,
Prophaze Delivers Frictionless WAF Control
Prophaze WAF fits into CI/CD pipelines and container orchestrations without SDKs or code changes—giving security teams real-time threat blocking across monoliths, microservices, and Kubernetes while DevOps ships faster and auditors stay happy.

Proxy-less deployment, zero app rewrites

Policy-as-code for GitOps and IaC workflows

Native Kubernetes and multi-cloud support

Granular RBAC with full audit compliance
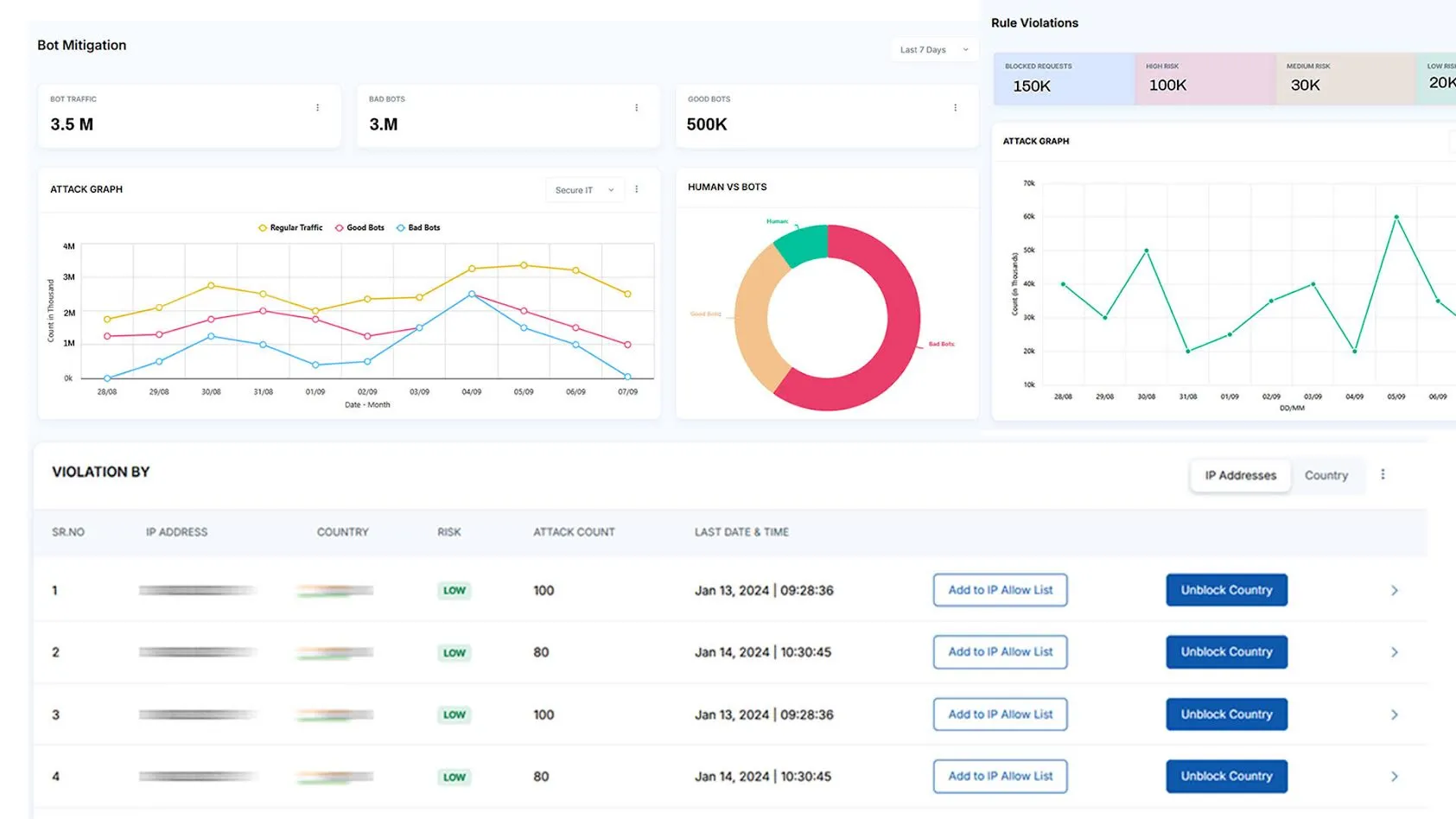
WAF Alerts Hard to Parse, Prophaze Puts It All in One Dashboard
Live attack maps by region, endpoint, and attack type
Trusted by High-Stakes Web Environments
Secure Your Web Applications with Prophaze WAF
- Start protecting your web applications and APIs with a WAF built for modern attack surfaces.