
What Is DNS Water Torture?
DNS Water Torture is a type of DDoS attack that targets the Domain Name System (DNS), a critical component of

DNS Water Torture is a type of DDoS attack that targets the Domain Name System (DNS), a critical component of

Jenkins is an open-source automation server that has emerged as a popular tool for streamlining software development workflows. In this

Connectionless Lightweight Directory Access Protocol (CLDAP) is a network protocol used for querying and modifying directory information services, such as

Description IBM OpenPages with Watson 8.3 and 9.0 could allow remote attacker to bypass security restrictions, caused by insufficient authorization

Generic Routing Encapsulation (GRE) is a tunneling protocol that encapsulates various network protocols within Internet Protocol (IP) packets. User Datagram
Simple Network Management Protocol (SNMP) is a widely used protocol for managing and monitoring network devices. It allows network administrators

As the holiday season is upon us and the festivities begin to heat up, at the very least, it also

The Simple Service Discovery Protocol (SSDP) is a network protocol used by devices to discover and communicate with each other

The Character Generator (CharGEN) protocol was originally designed for testing and debugging purposes. It allows a client to request a

UDP (User Datagram Protocol) is a connectionless protocol that allows data transmission between devices on a network. It is often

Prophaze Ensures Uncompromised Security on Safeguarding Confidential Customer Data With the increasing frequency of data breaches and cyberattacks in today’s
Application Programming Interfaces (APIs) play a vital role in modern software development, enabling communication and integration between different systems. However,

MicroK8s is a versatile tool for deploying Kubernetes clusters with minimal overhead. However, when dealing with production-like projects or even

What Are The Example Of A DDoS Attack? Uncover notable examples of DDoS attacks, their methods, their impact, and the

How Does A WAF Integrate With Other Security Solutions? Discover the seamless integration with IDS/IPS, SIEM, anti-malware, vulnerability scanners, authentication

What are the advantages of WAF? Discover how WAFs deliver all-encompassing defence, reduce vulnerabilities, improve data security, give real-time threat

Can WAF Protect DDoS Attacks? Determine the defense against DDoS attacks by Web Application Firewalls (WAF). Learn how WAFs can

Description Due to insufficient validation of parameters passed to the legacy HTTP query API, it is possible to inject crafted

What is Logging and Monitoring? In the world of cybersecurity, logging and monitoring play a critical role in protecting organizations
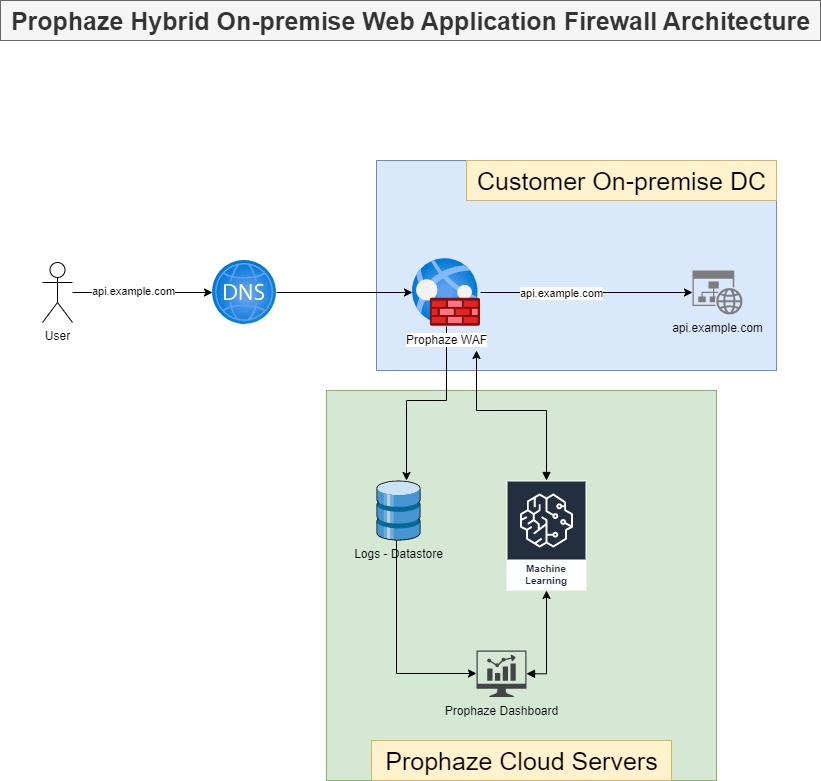
On-Premises WAF Prophaze WAF Supports On-Premises Prophaze WAF support on-premises deployment to ensure compliance with security in industries such as

What is PCI DSS? The Payment Card industry data security (PCI DSS), was unfolded to encourage and enhance card holder

What is Swagger? Swagger is the way of defining the structure of APIs (Application Programming Interface). Swagger is specifically developed

What is Container Runtime Protection? Container runtime protection provides security for containers during runtime. With the evolution of container technology,
Zero-Configuration Web Application and API Protection for Kubernetes Zero-Configuration Web Application and API Protection (WAAP), DDoS protection and Bot Mitigation