
CVE-2024-38319 : IBM SECURITY SOAR 51.0.2.0 CODE INJECTION
Description IBM Security SOAR 51.0.2.0 could allow an authenticated user to execute malicious code loaded from a specially crafted script.

Description IBM Security SOAR 51.0.2.0 could allow an authenticated user to execute malicious code loaded from a specially crafted script.

HTTPS cookies, essential for website functionality and user experience, become a security liability when not adequately secured. These small data

Description The Email Subscribers by Icegram Express plugin for WordPress is vulnerable to SQL Injection via the ‘hash’ parameter in

Description Envoy is a cloud-native, open source edge and service proxy. Envoyproxy with a Brotli filter can get into an

Insider threats refer to security risks caused by people inside an organization who are authorized to access confidential systems, data,

Prophaze’s Comprehensive Approach to API Security in the Patient-Centric Digital Health Era In the realm of modern healthcare, where digital

Description A remote code execution (RCE) vulnerability exists in the parisneo/lollms-webui, specifically within the ‘open_file’ module, version 9.5. The vulnerability

Description This High severity RCE (Remote Code Execution) vulnerability was introduced in version 5.2 of Confluence Data Center and Server.

Description The Element Pack Elementor Addons (Header Footer, Template Library, Dynamic Grid & Carousel, Remote Arrows) plugin for WordPress is
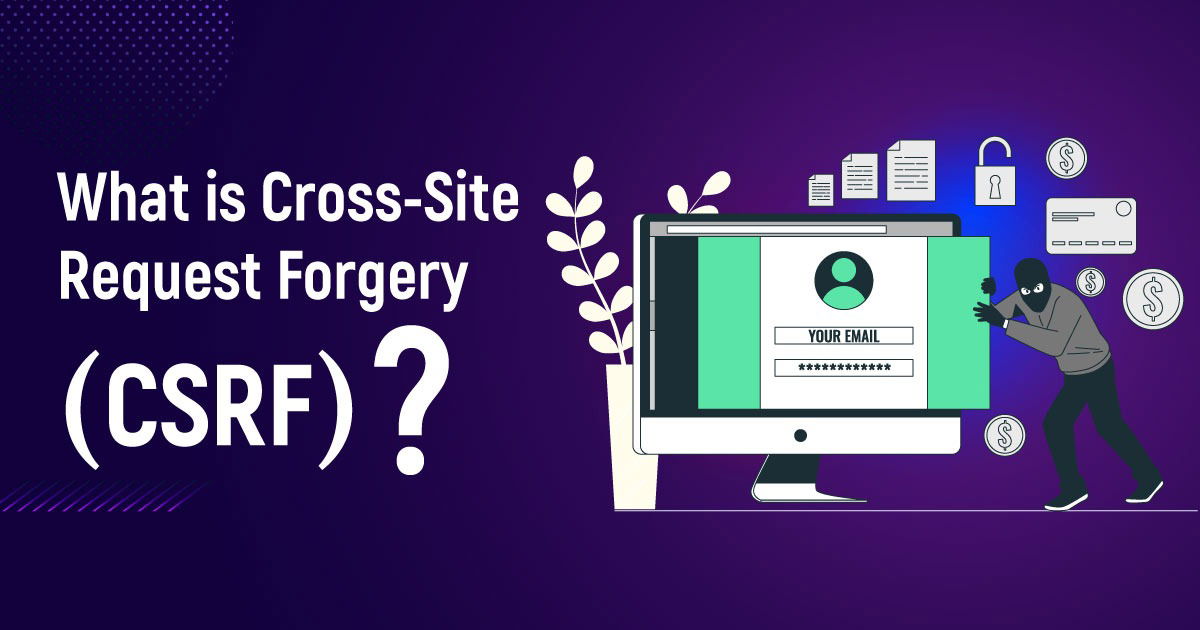
Cross-Site Request Forgery (CSRF) is an attack method that tricks users into performing an unwanted action on a website they

Description The Yoast SEO plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the ‘display_name’ author meta in all

In the realm of web security, the evolution of protocols brings both advancements and vulnerabilities. The HTTP/2 protocol, known for

Description Git is a revision control system. Prior to versions 2.45.1, 2.44.1, 2.43.4, 2.42.2, 2.41.1, 2.40.2, and 2.39.4, repositories with

Description IBM App Connect Enterprise 11.0.0.1 through 11.0.0.25 and 12.0.1.0 through 12.0.12.0 is vulnerable to HTML injection. A remote attacker

Description Due to an unsafe de-serialization method used by the Veeam Service Provider Console(VSPC) server in communication between the management

In our interconnected digital era, endpoints represent the gateways to an organization’s digital assets. Unfortunately, they also stand as prime

SlowLoris DDoS Attacks are a type of stealthy, low-and-slow layer 7 Distributed Denial of Service (DDoS) attack that targets web

Significant challenges have marked the cloud security landscape as organizations increasingly rely on cloud services. In 2023, 82% of data

Multicloud involves utilizing two or more cloud service providers, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud

Description Versions of the package mysql2 before 3.9.4 are vulnerable to Remote Code Execution (RCE) via the readCodeFor function due

Description Self-Registration and Modify your own profile in User Admin Application of NetWeaver AS Java does not enforce proper security

Continuous Integration (CI) focuses on frequently merging code changes from multiple developers into a shared repository. It involves automatically building

Description A problem has been identified in the CloudStack additional VM configuration (extraconfig) feature which can be misused by anyone

Description Memory corruption while redirecting log file to any file location with any file name. References https://docs.qualcomm.com/product/publicresources/securitybulletin/april-2024-bulletin.html For More Information