OWASP TOP 10
OWASP Top 10 Web Application Vulnerabilities’ Mitigation using Prophaze WAF
Prophaze web application firewall (WAF) that protects against various attacks. Prophaze recommends following the OWASP (Open Web Application Security Project) Top 10 security risks to ensure maximum protection against common web application security threats. Prophaze helps web application owners protect their applications against common threats. Prophaze WAF requires no additional configuration but it automatically updates to include protection against new vulnerabilities.
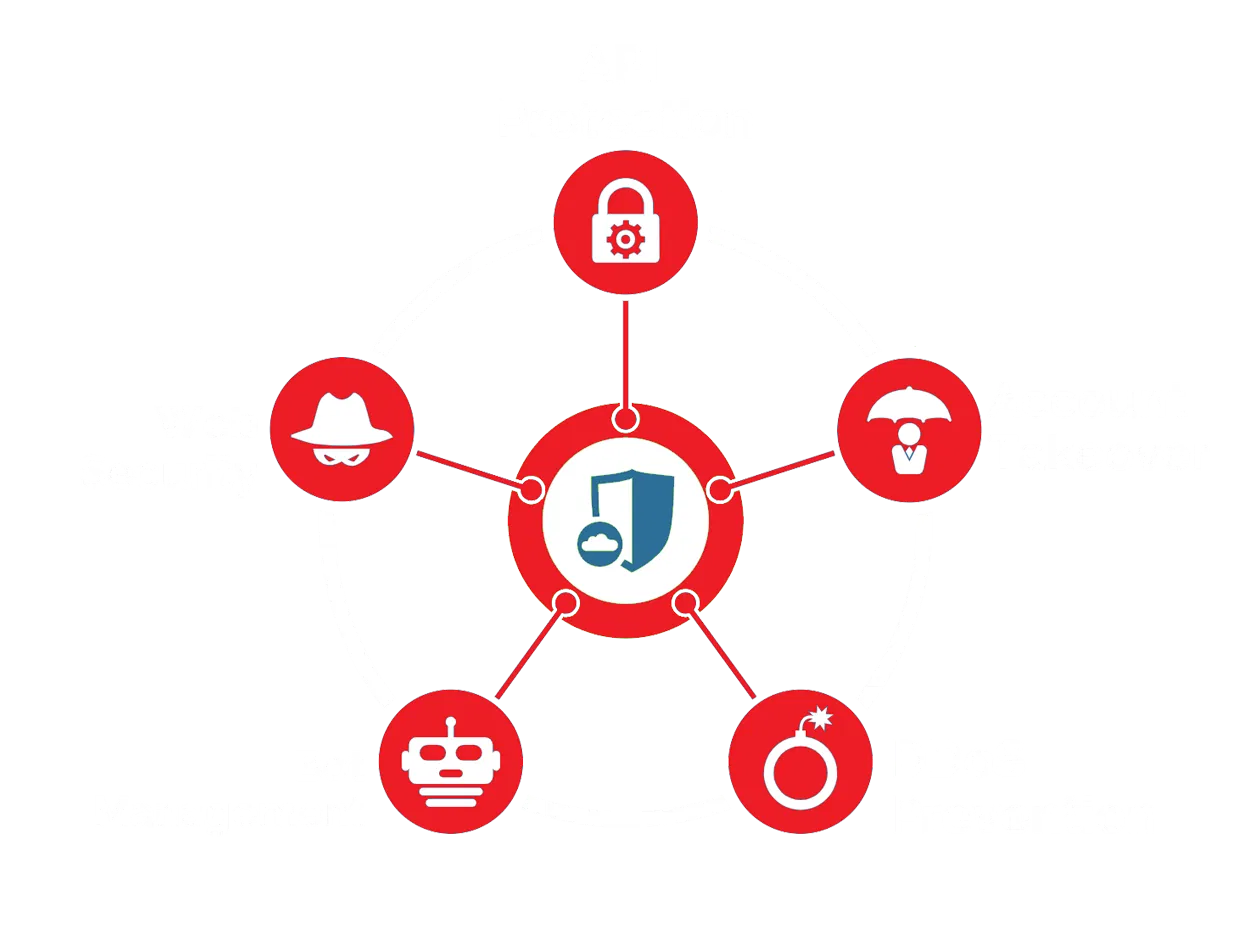

Enhancing Web Application Security with OWASP Top 10 Protection
The OWASP Top 10 vulnerabilities provide guidance to developers and security professionals on the most critical vulnerabilities that are commonly found in web applications. Prophaze protects common threats such as injection attacks, cross-site scripting (XSS), broken authentication and session management, insecure direct object references, security misconfiguration, insufficient logging and monitoring, insufficient input validation, broken access control, cross-site request forgery (CSRF). It is possible to create/modify rules to match patterns of exploitation attempts in HTTP/S requests and block requests from entering your servers using Prophaze WAF.
Mitigation using Prophaze WAF
These 10 application risks are dangerous because they may allow attackers to plant malware, steal data, or completely take over your computers or web servers. To make sure of availability and protect against abuse, it is possible to set API usage limits.
Prophaze WAF provides real-time website protection by using powerful cloud-based technologies to maintain protection against the latest threats. Prophaze will automatically scan your website for thousands of known vulnerabilities and OWASP Top 10. Prophaze also ensures that the web applications are protected against being used as threat vectors in the client’s network.

Benefits of Using Prophaze WAF over OWASP Top 10 Vulberabilities

Protecting Your Web Application from Injection Attacks
Prophaze can help by providing a set of predefined rules and customizable policies for input validation. Prophaze uses Parameterized filters to ensure that user input is treated as data rather than executable code. Use stored procedures to execute frequently used database operations. Stored procedures are precompiled SQL statements that are stored in the database and can help prevent SQL injection attacks. Prophaze provides real-time monitoring, rule-based filtering, and advanced threat detection to identify and block any attempts at injection attacks.
Preventing Cross-Site (XSS) Attacks with Prophaze WAF
To prevent cross-site XSS attacks, Prophaze uses HTTP-only and secure cookies to prevent attackers from accessing session data or stealing user credentials. Implement input validation mechanisms to ensure that user input is free of any malicious code. Implement a Content Security Policy (CSP) that can help prevent XSS attacks by blocking the execution of any scripts that are not from trusted sources. Prophaze provides real-time monitoring and advanced threat detection to identify and block any attempts at XSS attacks.


Securing Authentication and Session Management
To secure authentication and session management, Prophaze implements strong password policies that require users to create complex passwords that are difficult to guess or brute-force. Implement multi-factor authentication to provide an additional layer of security to the authentication process as a one-time password. Prophaze Provides session timeouts and inactivity logout mechanisms to ensure that users are automatically logged out after a period of inactivity. Prophaze provides real-time monitoring and advanced threat detection to identify and block any session hijacking.
Restricting Access with Insecure Direct Object Reference Protection
These attacks can result in unauthorized access to sensitive data or manipulation of the application’s functionality. Prophaze Implement access control mechanisms to ensure that users are only able to access the resources that they are authorized to access. This helps ensure that your web application is protected against these types of attacks. Session filter vulnerabilities patterns (XSS, detect predictable resources protection and components with known vulnerabilities), Allow list (File type and Methods). Provide protection on Role/IP/GEO-based policy, Directory traversal protection, Authentication, Reply Cookie Flags

Ensuring Strong Security Configuration with Prophaze
Ensuring strong security configuration helps protect against attacks and vulnerabilities in the application’s software and hardware components. Conduct regular security audits to identify any vulnerabilities in your application’. Prophaze does Parameters Filter, Path Blocking filter, Vulnerabilities filter (blocks predictable resources and known backdoors), Automatic policy generation, RFC enforcement, Native R/T Proxy, Error Masking (eg. Masking error 500s), Directory Listing Prevention, Masquerade Server Identity, Activity Tracking (prevents foreign scanners), Role/IP/GEO based policy, DAST (integration with web scanners), HSTS/Clickjacking, and API Security
Keeping Your Web Application Secure from Components with Know Vulnerabilities.
Prophaze implement XML security filter, JSON Parsing Properties, Vulnerabilities filters, Database filters, Parameters filter, Database filter, Path Blocking filter, Allow List filter, Vulnerabilities filter (blocks known patterns, backdoors, and predictable resource), Create custom patterns, Automatic policy generation, RFC enforcement, Create custom patterns, Error masking (eg: Masking error 500s), Directory Listing Prevention, Masquerade Server Identity, Activity Tracking (prevents foreign scanners), Role/IP/GEO based policy, Signature update mechanism, Source blocking feature, DAST (Integration with HP Web Inspect), Unvalidated Redirect, Reply Cookies Flags, and HSTS/Clickjacking
·

Detecting Security Breaches with Prophaze Monitoring
Detecting and responding to security breaches is critical for maintaining the security of your web application. A security breach can result in unauthorized access to sensitive data, theft of intellectual property, or disruption of your web application’s functionality. To detect and respond to security breaches with Prophaze monitoring by Safe Reply filter, Session filter, Vulnerabilities filter (Predictable Resource Location), Server error’s masking
Preventing XML External Entities(XXE) Attack with Prophaze Measures
XML External Entities (XXE) is a common attack vector for web applications that use XML parsing. In an XXE attack, an attacker can exploit vulnerabilities in an application’s XML parsing code to include external entities that can be used to read files, execute arbitrary code, or perform other malicious actions. To protect your web application Prophaze implements JSON Parsing property, Vulnerabilities filter, DB filters, Allow List filter, Tunnel’s Message size (max request body), and Unvalidated Redirect. Additionally, Prophaze offers customizable policies, granular controls, and comprehensive reporting to enable fine-tuned security measures

Preventing Insecure Deserialization with Prophaze WAF
Insecure deserialization is a common vulnerability in web applications that can lead to remote code execution, data tampering, and other malicious activities. Insecure deserialization occurs when an attacker is able to exploit vulnerabilities in an application’s deserialization code to execute arbitrary code or modify serialized objects. To protect your web application from attacks, Prophaze JSON Parsing property, Vulnerabilities filter, DB filters, and Parameters Filters. Additionally, Prophaze offers customizable policies, granular controls, and comprehensive reporting to enable fine-tuned security measures
Prophaze Comprehensive Logging and Monitoring Mechanisms.
Insufficient logging and monitoring is a common vulnerability in web applications that can lead to undetected security breaches, unauthorized access, and other malicious activities. Occurs when an application does not log enough information to adequately monitor and detect security breaches, Prophaze recommends the following measures. Prophaze filters Authentication (login monitoring), Defense Messaging, AppWall Forensics – Request/Response logging, APSolute Vision AVR, APSolute Vision Analytic, and SIEM system integration

