How WAF Works
Prophaze WAF
Prophaze’s WAF is a reliable and effective solution -to secure your web applications against cyber threats. Web application firewall effort in -configuration-deployment Customisation. In just a few minutes, you can fully implement to safeguard all of your applications from threats. Our fully featured application security service delivered via the cloud breaks the mold.

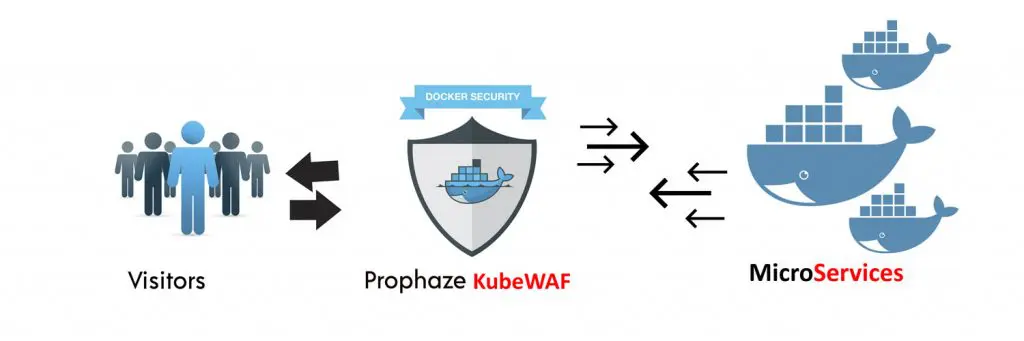
Kubernetes Waf For Your Cluster
Prophaze KubeWAF is an Enterprise Grade Kubernetes Web Application Firewall which is deployed as a microservice along with your other components. It will work alongside with cloud load balancer and filters all the incoming traffic towards your api services

Public Cloud Support
A web application running on a public cloud environment or multiple clouds, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform. Our WAF is equally available in every region in order to adequately reduce the absence of latency. Yet, in order to reduce latency, Prophaze WAF connects networks with customer enterprises. WAF’s rule sets decreases latency to less than 300 microseconds
The Prophaze WAF can be deployed in any public cloud such as AWS, GCP, AZURE, or Digital Ocean and on Private Cloud instances like Microk8s

AI Based WAF
Prophaze servers are equipped with Artificial Intelligence-based tools that monitor every request and categories those based on their previous threat score and take a decision to route that traffic. Where we monitor, test, detect, access controls, and authentication against cyber threats
Payload Scanning
Prophaze is a new generation web application firewall which intelligently tracks down malicious request into your Web APIs . It uses multiple attack detection algorithms to monitor all the incoming requests and will pass only legitimate requests to the host server


Layer 7 DDoS Protection
Prophaze protects your applications from distributed denial of service DDoS attacks by malicious bot networks. The offender initiates a lot of requests to overwhelm the target(s) and uses several compromised or controlled sources to launch the attack.
