OWASP Top 10: 2017 Edition in Comparison with 2013 Edition
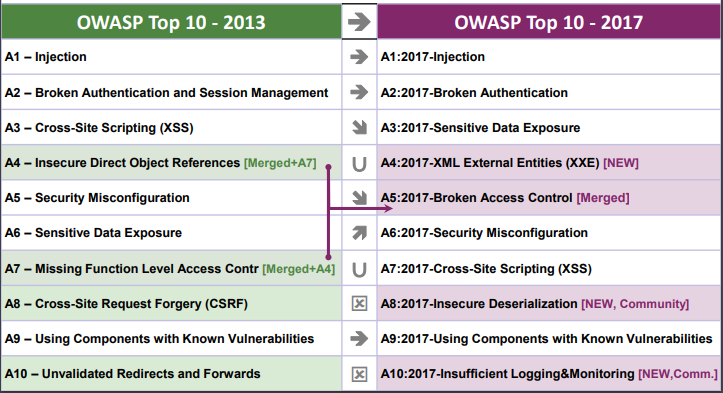
Image Source: https://owasp.org/www-pdf-archive/OWASP_Top_10-2017_%28en%29.pdf.pdf
Major Changes Introduced from 2013 to 2017
Change has accelerated in the course of the last four years, and the OWASP Top 10 is expected to change. We’ve totally refactored the OWASP Top 10, revamped the approach, used another data call process, worked with the local area, re-ordered our dangers, re-reviewed each hazard from the beginning, added references to frameworks and languages that are presently normally utilized.
In the course of the last couple of years, the fundamental innovation and architecture of applications have been modified significantly:
- Microservices being written in node.js & Spring Boot are replacing traditional solid applications. Microservices accompany their own security challenges, including establishing trust between microservices, containers, secret management, and so on. Old code never expected to remain accessible from the Internet is presently sitting behind an API or RESTful web service to be devoured by Single Page Applications (SPAs) and mobile applications. Architectural assumptions by the code, like confided in callers, are, as of now, not valid.
- Single-page applications, written in JavaScript frameworks like Angular and React, allow the creation of exceptionally modular feature-rich front finishes. Customer-side functionality that has traditionally been conveyed server-side brings its own security challenges.
- JavaScript is presently the primary language of the web with node.js running server-side and current web frameworks, for example, Bootstrap, Electron, Angular, and React running on the customer.
New Issues, Backed by Data:
- A4:2017-XML External Entities (XXE) is another category primarily supported by source code analysis security testing tools (SAST) data sets.
New Issues, Backed by the Local Area:
We asked the local area to give an understanding into two forward-looking weakness categories. After more than 500 friend entries and eliminating issues that were already supported by data (like Sensitive Data Exposure & XXE), the two evolving issues are:
- A8:2017-Insecure Deserialization, which grants remote code execution/sensitive object manipulation on the respective platforms.
- A10:2017-Insufficient Logging & Monitoring, the lack of which can forestall or significantly delay malicious activity and breach detection, incident response, and digital forensics.
Consolidated or Resigned, Yet Entirely Not Forgotten:
- A4-Insecure Direct Object References and A7-Missing Function Level Access Control converged into A5:2017-Broken Access Control.
- A8-Cross-Site Request Forgery (CSRF), as many frameworks incorporate CSRF defenses, it was found in just 5% of applications.
- A10-Unvalidated Redirects and Forwards, while found in approximately 8% of applications, it was defeated overall by XXE.











