What is Directory Traversal?
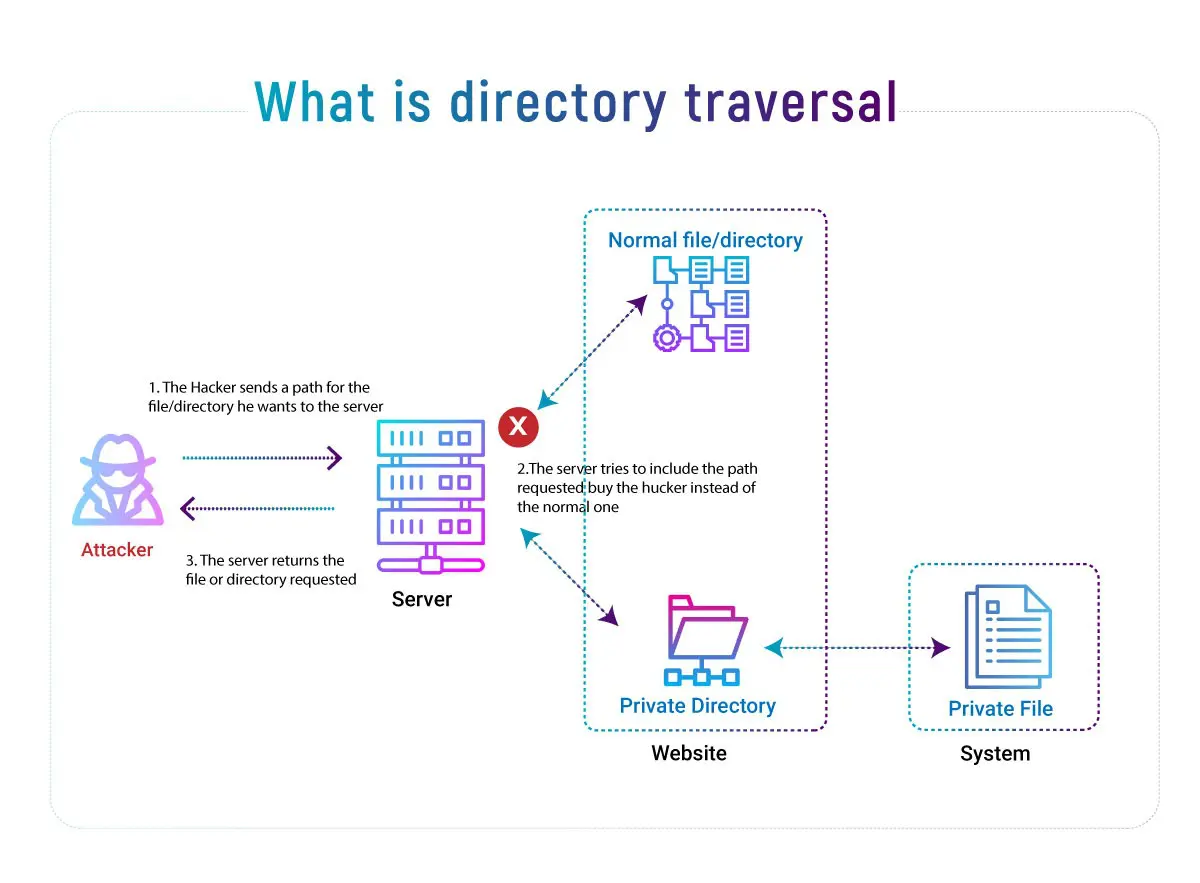
Directory traversal is also known as file path traversal. It is a web security flaw that enables an attacker to access any file on the server hosting an application. This may comprise sensitive operating system files, application code and data, and back-end system login information. In some circumstances, an attacker may be able to write arbitrary server files, which would give them the ability to change application data or behaviour and ultimately seize total control of the server.
The best approach to protect against file path traversal flaws is to never transmit user-supplied input to filesystem APIs. A lot of these application functions can be modified to give the same behaviour in a safer manner.
If passing user-supplied input to filesystem APIs is deemed necessary, then two lines of security should be combined to fend off attacks:
The user input should be verified by the application before processing it. The validation should, ideally, compare to a whitelist of authorized values. If the needed functionality prevents that, then the validation should ensure that the input only contains content that is allowed, such as only alphanumeric characters.
The application should append the input to the base directory after validating the provided input and use a platform filesystem API to canonicalize the path. It should ensure that the canonicalized path begins with the anticipated base directory.












