Runtime Application Self-Protection (RASP)
Runtime Application Self-Protection (RASP) does protect itself from many vulnerabilities in the enterprise by identifying and blocking attacks in real-time. RASP’s identification and security features operate on the server the app’s running on; therefore the technology doesn’t affect the application’s design.
RASP can protect both web and non-web applications from malicious input or behavior by analyzing both the app’s behavior and the context of that behavior. By continuously observing its behavior, attacks can be identified and mitigated quickly without any manual interference.
- Ensures the application is secure by intercepts all calls from the app to a system.
- Incorporates security into a running application wherever it resides on a server
- Validates data requests directly inside the app.
- Enhances the entire application security by keep track of inputs and stopping those that may allow attacks.
- Secure the runtime environment from unwanted changes and tampering.
- Provides security-in-depth and dramatically reduces the chances of security breaches.
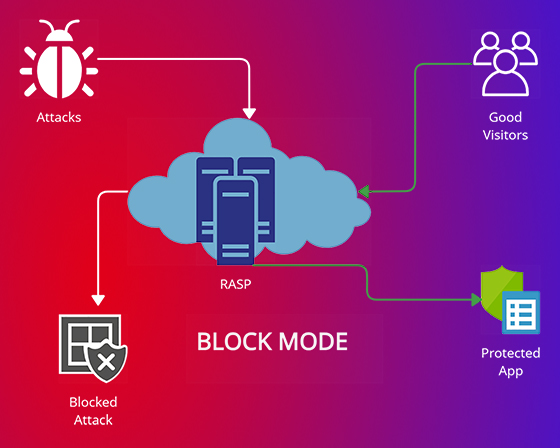
HOW DOES RASP WORK?
RASP takes control of the app and addresses the issue when a security incident occurs in an application.
- In monitor/ diagnostic mode, it records and alerts attacks to vulnerable points but won’t block requests.
- In protection/block mode, it stops malicious requests to vulnerable points
Terminating a user’s session, blocking an application’s execution, or notifying the user or security personnel are the other actions that RASP can take.
- RASP can thwart attacks with high accuracy.
- Full visibility of the internal architecture details of the applications.
- Complete visibility of the execution flow during runtime (distinguish between what is an attack and what is not.)
- RASP will only intervene if a payload hits a truly vulnerable point of the application, resulting in better performance, and also can distinguish between actual attacks and legitimate requests for information, which reduces false positives.
- The combination of static and dynamic points of view can address many serious OWASP Top 10 risks that can be protected.

BENEFITS OF A RASP
- Strong protection, including zero-days
- Easy maintenance
- Adaptability to new standards
- Cloud support (No need to update network and firewall rules.)
- DevSecOps support
- Providing enough visibility into application layer attacks
Prevent from DDoS and other attacks
Prophaze WAF can reduce the load on its website, this checks for SQLi attacks and XSS attacks for both the network and application layers
When individuals comes to a website for help, some offenders can work to compromise the application or steal any valuable information. These people can also launch a DDoS attack make the application unavailable.
