What is DNS and how does it work?
DNS is the abbreviation for Domain Name System. The task of the DNS is to act like a Translator between humans and machines (computer) by translating the human identifiable domain names to machine readable IP addresses, and is essentially the base for accessing information on the internet. This process constitutes the DNS protocol. DNS is a combination of various servers like recursive resolvers and root, top-level and authoritative name servers. When a website is entered in the web browser, it sends a DNS query to the recursive resolver which is usually managed by the Internet Service Provider (ISPs) and if the requested data is in its Cache it is served back. Otherwise, the request is forwarded to the root server, top-level domain or TLD server and finally, the authoritative name server.
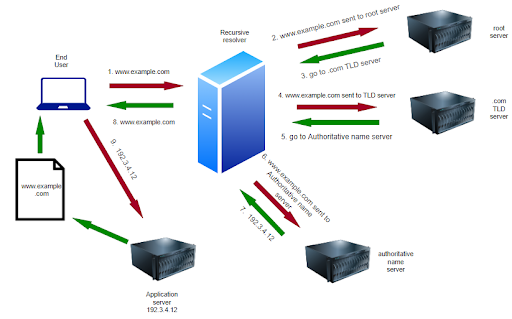
The authoritative name servers are the ones that contain the actual mapping between domain names and IP addresses. To reduce the number of requests that an authoritative name server gets, the results of a DNS query are cached at various levels like your personal device, internet routers and ISPs. All of these improve the operational speed and efficiency of the authoritative name server.
Need for DNS Security
The advent of DNS took place in the 1980s when the internet was much smaller and not security oriented. One of the biggest challenges with DNS was the lack of means to verify the authenticity of the responses obtained from the DNS. Only the source IP of the response can be identified by the resolver which is easily spoofed. Any attacker could meddle with the DNS response by impersonating an authoritative server and misdirect the clients to potentially malicious websites. And if this tampered response is cached by the recursive resolver, it could lead to a widespread compromise of client systems. The caching of such blemished responses is termed as cache poisoning which is a kind of DNS attack.
In DNS attacks, the two primary attack types are Authoritative attacks and Caching Recursive attacks. Authoritative attacks include DDoS attacks, Amplification attacks, or Reflection attacks, to name a few. Caching Recursive attacks, such as Cache Poisoning attacks, or DNS Hijacking attacks. Just like wine, there are also a few outliers, such as DNS Tunneling attacks. However, most DNS attacks are either Authoritative or Caching Recursive.
The process of securing DNS is complicated because, unlike most other protocols, the principal purpose of DNS is to both publish information as well as allow clients to access that information. So, the methods we use to defend DNS, often have to stay away from the classic, simple blocking techniques.
The exponential growth in internet usage has increased the attack surface proportionally, leading to a higher potential and volume of compromised clients. Hence, it becomes necessary to fortify the defenses of the DNS protocol for a secure browsing experience.
What is DNS Security Extensions (DNSSEC)? How does it work?
One such method for securing the DNS is DNSSEC which is an abbreviation for DNS Security Extensions and whose development started in the 1990s, adds authentication using digital signatures on public-key cryptography protecting against attacks like cache poisoning. In other words, DNSSEC attempts to verify the authenticity of responses sent by name servers to clients, using cryptographic signature technology. DNSSEC adds cryptographic signatures to DNS records, which protects data published in the DNS which in turn helps in validating the data with the authoritative DNS server. They are called extensions, since DNS queries are not capable of securing themselves.
Public key cryptography uses a pair of keys termed as private keys and public keys. They help validate that the query response from the DNS wasn’t spoofed or modified and contains the original record. Moreover, they also provide message integrity ie., they help confirm that the messages weren’t changed during transmission. However, they can only be used for validation purposes and cannot encrypt the data in transit leaving it readable in plain text though it becomes almost impossible to tamper with this information.
With DNSSEC, the entire DNS resolution process is the same as DNS. The only addition is that the DNS queries have the public signature attached and also, all the records in every consecutive server are signed with a private key. DNSSEC specifically provides exceptional defense against cache poisoning attacks making it impossible for the attackers to impersonate the authoritative name servers.
Wrapping up
Securing DNS is vital as it forms the foundation of the internet. Without DNS, information transfer across the internet would not be possible. Hence, it has become an attractive target for attackers. DNSSEC, one of the first defense mechanisms built for DNS security in the 1990s, induced the need for protection of DNS. Though it is incapable of preventing advanced attacks like DDoS, it does help avert a powerful attack like the cache poisoning.









