Blogs
- Latest Blog
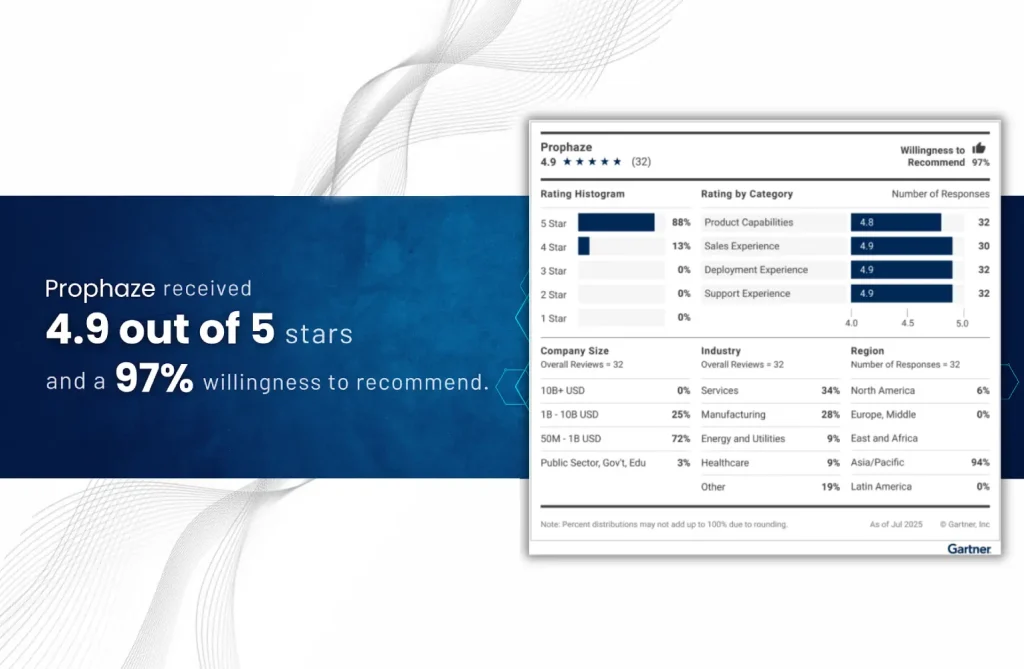
“Voice of the Customer” 2025 for Cloud Web Application and API Protection
- Blog
Artificial intelligence is no longer limited to generating responses or summarizing information. Modern AI systems
- Blog
Kubernetes Web Application and API Protection (KWAAP) has become essential as traditional WAFs only secure
- Blog
Is Your Azure Cloud Security Enough? Enterprises running mission-critical workloads on Microsoft Azure are increasingly
- Blog
What Is the DPDP Act of India India’s Digital Personal Data Protection Act (DPDP Act)
- Blog
Understanding Cybersecurity Awareness Month 2025 October marks Cybersecurity Awareness Month (CSAM)—an annual initiative encouraging individuals,
- Blog
A Layer 7 attack—also called an application-layer DDoS attack—is one of the most severe threats
- Blog
In 2025, managed security service providers (MSSPs) are at the center of enterprise defense. With
- Blog
In 2025, Indian enterprises face unprecedented cyber threats — from AI-powered ransomware to shadow API
- Blog
APIs power the modern digital world — from mobile apps and SaaS platforms to enterprise
- Blog
Why India is Emerging as a Cybersecurity Powerhouse Cybersecurity has become one of the most
- Blog
In 2025, protecting your web applications and APIs is no longer just an IT concern
- Blog
India’s rapid digital transformation has opened the floodgates to cyber threats. As industries shift toward